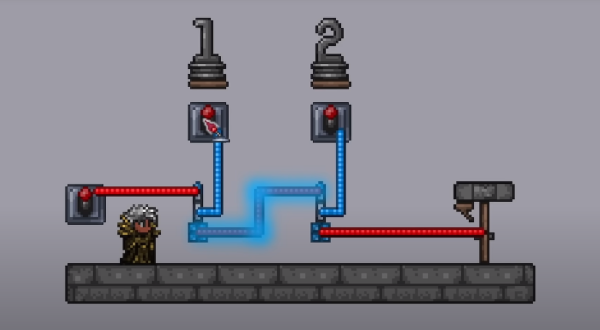
[Xander Naumenko] has created something truly impressive — a working RISC-V CPU completely contained in a Terraria world. And then for added fun, he wrote the game of pong, playable in real time, from within the game of Terraria. It’s all based on the in-game wiring system, combined with a bit of a hack that uses the faulty lamp mechanic to create a very odd AND gate. In Terraria, the existing logic gates have timing issues that make them a no-go for complicated projects like this one. The faulty lamp is intended to do randomized outputs, by stacking multiple inputs to get a weighted output when a clock signal is applied. The hack is to simply give this device a single input, turning it into a clocked IF gate. Two of them together in series makes a clocked AND gate, and two in parallel make a clocked OR gate.
Why would [Xander] embark on this legendary endeavor? Apparently after over eight thousand hours clocked in game, one gets a bored of killing slimes and building NPC houses. And playing with the game’s wiring system turned on a metaphorical lightbulb, that the system could be used to build interesting systems. A prototype CPU, with a completely custom instruction set came next, and was powerful enough to compute Fibonacci. But that obviously wasn’t enough. Come back after the break for the rest of the story and the impressive video demonstration.
Continue reading “This RISC-V CPU Games In Rust From Inside The Game”