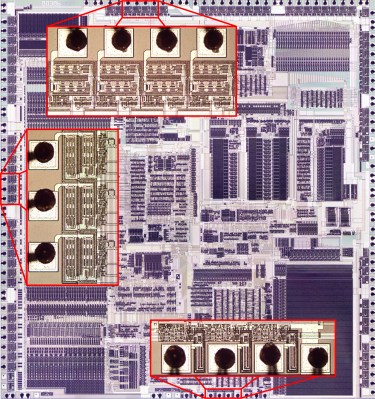
The best part about post-mortem teardowns of electronics is when you discover some unusual design features, whether or not these are related to the original fault. In the case of a recent [DiodeGoneWild] video involving the teardown of an industrial DIN-rail mounted 24 V, 960 Watt power supply, the source of the reported bang was easy enough to spot. During the subsequent teardown of this very nicely modular PSU the automatic power factor correction (APFC) board showed it to have an unusual design, which got captured in a schematic and is explained in the video.
Choosing such a APFC design seems to have been done in the name of efficiency, bypassing two of the internal diodes in the bridge rectifier with the external MOSFETs and ultrafast diodes. In short, it prevents some of the typical diode voltage drops by removing diodes in the path of the current.
Although not a new design, as succinctly pointed out in the comments by [marcogeri], it’s explained how even cutting out one diode worth of voltage drop in a PSU like this can save 10 Watt of losses. Since DIN rail PSUs rarely feature fans for active cooling, this kind of APFC design is highly relevant and helps to prevent passively cooled PSUs from spiraling into even more of a thermal nightmare.
As for the cause behind the sooty skid marks on one of the PCBs, that will be covered in the next video.
Continue reading “Very Efficient APFC Circuit In Faulty Industrial 960 Watt Power Supply”