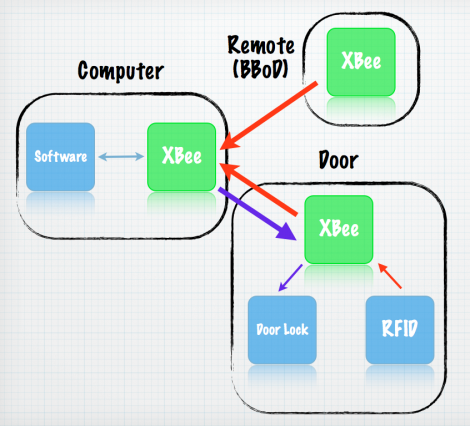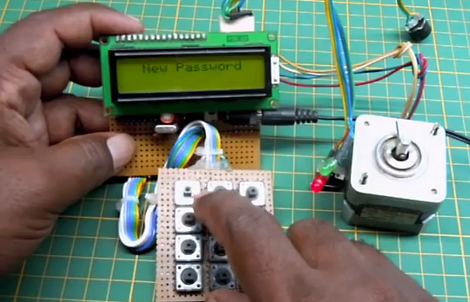
[Arshad Pathan] let us know about his latest project, a modular code lock that can be adapted to many different situations.
The user interface is made up of a character LCD screen and a 3×4 keypad. For this example [Arshad] is using a stepper motor as the locking mechanism. When the board is first powered up it runs the stepper in one direction until receiving input from a limiting switch. In this way, the microcontroller calibrates itself to ensure the lock is in a known position. From there it waits for user input. An unlocked door can be locked at any time by pressing the * key. Unlocking requires entry of the correct password. And a password can be changed by entering 9999 (followed by the old password when prompted).
In the video after the break [Arshad] does a great job of demonstrating the various modes which he has programmed. This stands on its own, but we always love to have more details so we’ve asked if [Arshad] is willing to share a schematic and the source code. We’ll update this post if we hear back from him.
Update: [Arshad] sent in a couple of schematics which can be found after the break.
Continue reading “Full Featured Security Lock Demonstration”