Hackaday forum member [Emeryth] recently posted his newest creation, the Wifon 2.0, which is an update to a project we featured last year. The second iteration of the device looks to make several improvements on the already solid concept.
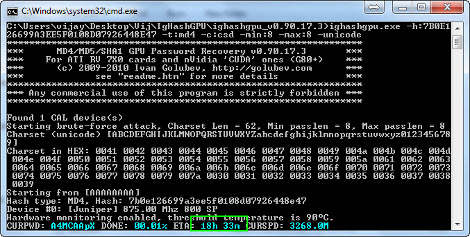
Ditching the simple 16×4 LCD, version 2 sports a full color 320×240 touch panel LCD. A faster STM32 micro controller replaces the Atmega88 he used the first time around, allowing him to create a much more advanced user interface. The micro runs the ChibiOS/RT real time operating system, which enables multitasking, making the entire project a lot easier. Like the first version, an original Fonera performs all of the pen testing, though this time around he has ditched the vanilla DD-WRT distro for Jasager, which is purpose-built for running the Karma attack.
The project is coming along nicely, and [Emeryth] says he has a few simple apps running on the device already. He has found that running several applications on the device simultaneously is testing the practical limits of the Foneras capabilities, though he may add more memory to the router in order to squeeze a little more life out of it.
[via Hackaday forums]