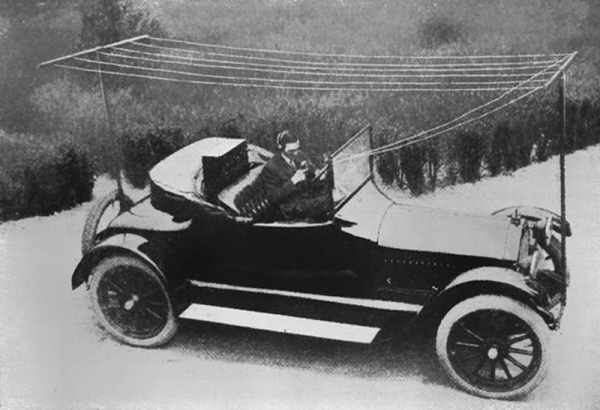
You used to be able to tell a die-hard ham radio operator on the road by the number and length of antennas protruding porcupine-like from their vehicle. There are still some mobile high frequency operators that have respectable car-mounted antenna farms, but they have nothing on Alfred H. Grebe. In 1919, he fitted a medium wave transmitter in his car that operated around 2 MHz. Since it needed a very large antenna, Grebe rigged a wire antenna that looked like a clothesline between the two bumpers. Obviously, you had to stop, set up your antenna, and then operate — you couldn’t talk and drive. But this may have been the world’s first automotive radio setup for voice communication.
The car had a separate battery for the radio and a dynamotor to generate high voltage for the tubes. Although many radio enthusiasts found ways to add receivers to their cars in the 1920s, it would be 1930 before Motorola made radios especially for cars in production quantities.