The war on Internet ads rages on, as the arms race between ad blockers and ad creators continues to escalate. To make a modern Internet experience even remotely palatable, plenty of people are turning to DNS-level filters to stop the ads from coming into the network at all. This solution isn’t without its collateral damage though, as the black lists available sometimes filter out something that should have made it to the user. For those emergencies, [Kristopher] created the Pie Stop, a physical button to enact a temporary passthrough on his Pi-Hole.
While [Kristopher] is capable of recognizing a problem and creating the appropriate white list for any of these incidents, others in his household do not find this task as straighforward. When he isn’t around to fix the problems, this emergency stop can be pressed by anyone to temporarily halt the DNS filtering and allow all traffic to pass through the network. It’s based on the ESP-01S, a smaller ESP8266 board with only two GPIO pins. When pressed, it sends a custom command to the Pi-Hole to disable the ad blocking. A battery inside the case allows it to be placed conveniently anywhere near anyone who might need it.
With this button deployed, network snafus can be effectively prevented even with the most aggressive of DNS-level ad blocking. If you haven’t thought about deploying one of these on your own network, they’re hard to live without once you see how powerful they are. Take a look at this one which also catches spam.






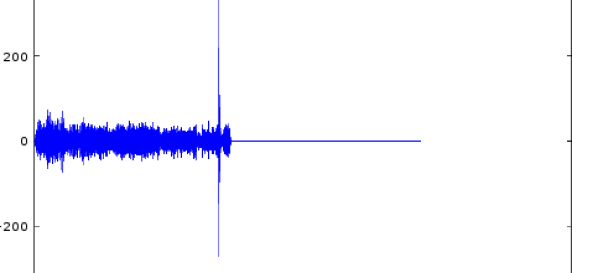
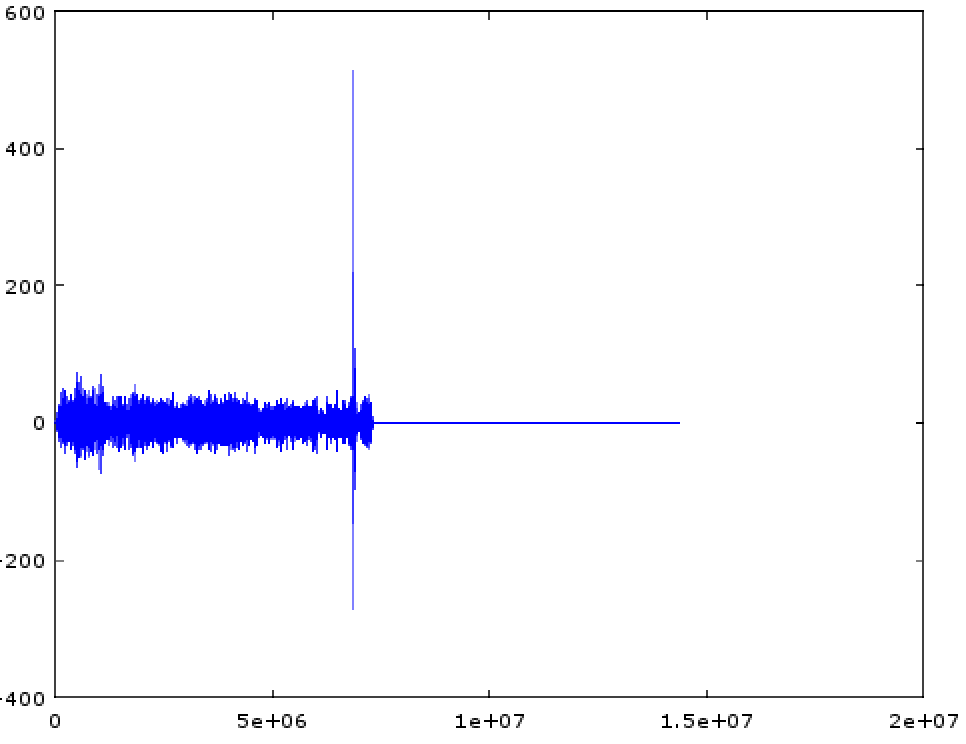 [tomek] was aware of this hip knowledge domain called Digital Signal Processing but hadn’t done any of it themselves. Like many algorithmic problems the first step was to figure out the fastest way to bolt together a prototype to prove a given technique worked. We were as surprised as [tomek] by how simple this turned out to be. Fundamentally it required a single function – cross-correlation – to measure the similarity of two data samples (audio files in this case). And it turns out that
[tomek] was aware of this hip knowledge domain called Digital Signal Processing but hadn’t done any of it themselves. Like many algorithmic problems the first step was to figure out the fastest way to bolt together a prototype to prove a given technique worked. We were as surprised as [tomek] by how simple this turned out to be. Fundamentally it required a single function – cross-correlation – to measure the similarity of two data samples (audio files in this case). And it turns out that 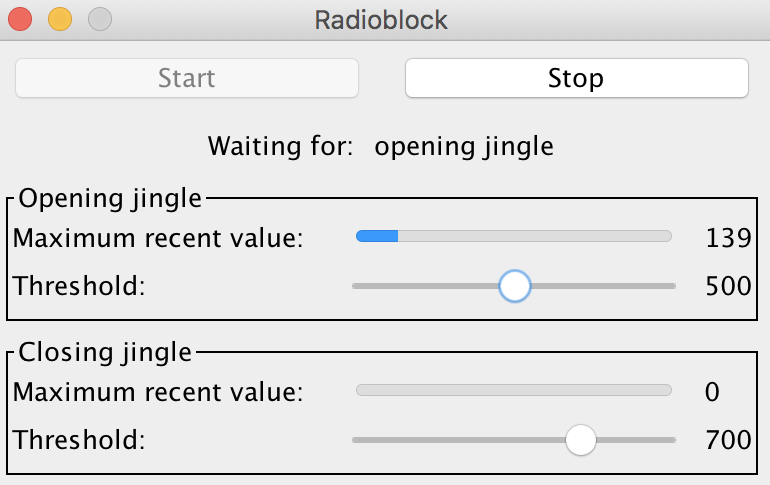 At this point all that was left was packaging it all into a one click tool to listen to the radio without loading an entire analysis package. Conveniently Octave is open source software, so [tomek] was able to dig through its sources until they found the bones of the critical xcorr() function. [tomek] adapted their code to pour the audio into a circular buffer in order to use an existing Java FFT library, and the magic was done. Piping the stream out of ffmpeg and into the ad detector yielded events when the given ad jingle samples were detected.
At this point all that was left was packaging it all into a one click tool to listen to the radio without loading an entire analysis package. Conveniently Octave is open source software, so [tomek] was able to dig through its sources until they found the bones of the critical xcorr() function. [tomek] adapted their code to pour the audio into a circular buffer in order to use an existing Java FFT library, and the magic was done. Piping the stream out of ffmpeg and into the ad detector yielded events when the given ad jingle samples were detected.