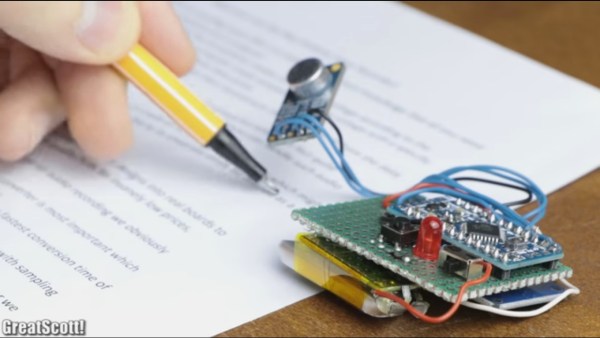
What we like most about [GreatScott’s] project videos is that he not only shows making them but also the calculations for selecting parts and the modifications along the way. This time he’s made a mini spy bug that records up to nine hours of audio.
His first task was to figure out if the ATmega328p’s ADC is suitable for audio sampling, but only after he explains how sampling works by periodically checking the input voltage from the microphone. Checking the datasheet he found that the ADC’s fastest conversion time is 13 microseconds, which works out to a sampling rate of 76.923 kHz. Good enough.
He then walks through why and how he decided to go with a pre-made amplifier circuit built around the MAX9814 IC. Spoiler alert. His electret’s amplifier output voltage was too low, using an off-the-shelf circuit instead of making his own kept things simple, and the circuit has automatic gain control.
At this point, he added the MicroSD card adapter. Why not just transmit the audio over FM as so many others have done with their hacks? Perhaps he’s worried about someone detecting the transmission and finding his bug.
His final optimization involved getting a good battery life. He measured the circuit’s current draw at 20 milliamps. With a 160 mAh battery capacity, that would be 8 hours of recording time. Removing the Arduino Pro Mini’s voltage regulator and two LEDs got the current down to 18 milliamps and a recording time of 9 hours. Better.
Those are the highlights. Enjoy his full walkthrough in the video below.