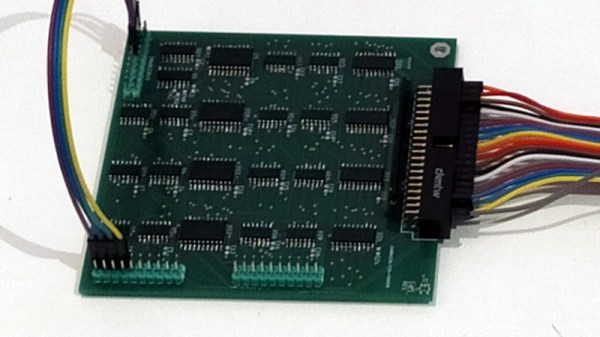
If you owned a classic Commodore home computer you might not have known it at the time, but it would have contained a versatile integrated circuit called the MOS6526. This so-called CIA chip, for Complex Interface Adaptor, contained parallel and serial ports, timers, and a time-of-day counter. Like so many similar pieces of classic silicon it’s long out of production, so [Daniel Molina] decided to replicate a modern version of it on a PCB using 74HGT CMOS logic.
The result will be a stack of boards board that appear to be about the size of a 3.5″ floppy disk covered in surface-mount 74 chips, and connected to the CIA socket of the Commodore by a ribbon cable. The base board is the only one completed so far and contains the data direction registers and parallel ports, but the succeding boards will each carry one of the chip’s other functions.
It seems rather odd to use so much silicon to recreate a single chip, but the point is not of course to provide a practical CIA replacement. Instead it’s instructive, it shows us how these interfaces work as well as just how much circuitry is crammed into the chip. It’s no surprise that it’s inspired by the C74 Project, a TTL 6502 processor that we featured last year.





 When you have a virtually unlimited budget, you can pull off some amazing things. This has become most evident recently as the CIA has been
When you have a virtually unlimited budget, you can pull off some amazing things. This has become most evident recently as the CIA has been 








