Sounds like somebody had a really bad day at work, as Western Digital reports that “factory contamination” caused a batch of flash memory chips to be spoiled. How much, you ask? Oh, only about 7 billion gigabytes! For those of you fond of SI prefixes, that’s 7 exabytes of storage; to put that into perspective, it’s seven times what Google used for Gmail storage in 2012, and enough to store approximately 1.69 trillion copies of Project Gutenberg’s ASCII King James Version Bible. Very few details were available other than the unspecified contamination of two factories, but this stands poised to cause problems with everything from flash drives to phones to SSDs, and will probably only worsen the ongoing chip shortage. And while we hate to be cynical, it’ll probably be prudent to watch out for any “too good to be true” deals on memory that pop up on eBay and Ali in the coming months.
flash126 Articles
Proto-PDA Regains Its Memory With The Help Of A Raspberry Pi Pico
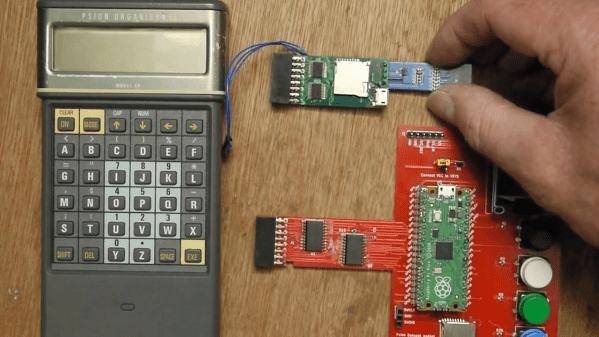
Remember the Psion Organiser? If you do, chances are you were an early adopter, as the 8-bit pocket computer had its heyday in the mid-1980s. Things have come a long way since then, of course, but just how far is illustrated nicely by the fact that a Raspberry Pi Pico can stand in for the Psion’s original memory packs.
Like many of the early attempts at putting a computer in your pocket, the Psion II had removable modules, which were dubbed “Datapaks”. The earliest versions of the Datapaks were little more than an EPROM chip on a small PCB, and the technical limitations of the day plus the quirky way of addressing the memory made it possible for [Amen] to mimic a Datapak using a modern microcontroller.
The first version was a breakout board that extended out of the Datapak slot significantly, with a Pico, OLED display, SD card slot, and a bunch of pushbuttons. That prototype proved that the Pico was indeed fast enough to fool the Psion into thinking a legit Datapak was plugged in. [Amen] later refined the design by making a board that stuffs everything into the Datapak slot, with the exception of the OLED which still dangles out where it can be seen. He puts the faux memory to the test in the video below.
It’s great to see groundbreaking tech of yesteryear like the Psion being taken care of and returned to use. We’ve seen others try before; here’s a hack that uses a Pi to connect a Psion Organiser to the internet through its RS-232 serial port.
Continue reading “Proto-PDA Regains Its Memory With The Help Of A Raspberry Pi Pico”
School Surplus Laptop BIOS Hacked To Remove Hardware Restrictions
Why did [Hales] end up hacking the BIOS on a 10 year old laptop left over from an Australian education program? When your BIOS starts telling you you’re not allowed to use a particular type of hardware, you don’t have much of a choice.
Originally [Hales] planned on purchasing a used Lenovo X260 to replace his dying laptop, but his plans were wrecked. A pandemic-induced surge in demand that even the used laptop market caused prices to bloat. The need for a small and affordable laptop with a built in Ethernet port led to the purchase of a Lenovo Thinkpad x131e. Although the laptop was older than he liked, [Hales] was determined to make it work. Little did he know the right-to-repair journey he was about to embark on.
Problems first arose when the Broadcom WiFi adapter stopped working reliably. He replaced it, but the coaxial antenna cable was found to be damaged. Even after replacing the damaged cabling, the WiFi adapter was still operating very poorly. Recalling past problems with fickle Broadcom WiFi adapters, it was decided that an Intel mPCIe WiFi adapter would take its place. When power was re-applied, [Hales] was shocked to find the following message:
Unauthorized network card is plugged in – Power off and remove the miniPCI network card
And this is where things got interesting. With off the shelf SOIC8 clips and a CH340 programmer, [Hales] dumped the BIOS from the laptop’s flash chip to another computer and started hacking away. After countless hours of researching, prodding, hacking, and reverse engineering, the laptop was useful once again with the new Intel WiFi adapter. His site documents in great detail how he was able to reverse engineer the BIOS over the course of several days.
But that’s not all! [Hales] was also able to modify the hardware so that his slightly more modern mPCIe WiFi adapter would come back on after the computer had been put in Hibernation. It’s an elegant hack, and be sure to check [Hales’] site to get the full details. And at the end, there’s a nice Easter egg for anybody who’s ever wanted to make their laptop boot up with their own logo.
We applaud [Hales] for his fine efforts to keep working equipment out of the landfill. We’ve covered many hacks that had similar goals in the past. Do you have a hack you’d like to share? Submit it via the Tips Line.
Cloned Memory Module Fixes Broken Scopemeter
Finding broken test gear and fixing it up to work again is a time-honored tradition among hackers. If you’re lucky, that eBay buy will end up being DOA because of a popped fuse or a few bad capacitors, and a little work with snips and a soldering iron will earn you a nice piece of test gear and bragging rights to boot.
Some repairs, though, are in a class by themselves, like this memory module transplant for a digital scopemeter. The story began some time ago when [FeedbackLoop] picked up a small lot of broken Fluke 199C scopemeters from eBay. They were listed as “parts only”, which is never a good sign, and indeed the meters were in various states of disassembly and incompleteness.
The subject of the video below was missing several important bits, like a battery and a power connector, but most critically, its memory module. Luckily, the other meter had a good module, making reverse engineering possible. That effort started with liberating the two RAM chips and two flash chips, all of which were in BGA packages, from the PCB. From there each chip went into a memory programmer to read its image, which was then written to new chips. The chip-free board was duplicated — a non-trivial task for a six-layer PCB — and new ones ordered. After soldering on the programmed chips and a few passives, the module was plugged in, making the meter as good as new.
While we love them all, it’s clear that there are many camps of test gear collectors. You’ve got your Fluke fans, your H-P aficionados, the deep-pocketed Keithley crowd — but everyone loves Tektronix.
Continue reading “Cloned Memory Module Fixes Broken Scopemeter”
Can You Hot-Swap Flash Chips In A Consumer Router?
Sometimes, you mess up when toying with the firmware of an embedded device and end up “bricking” what you were working on. [Chris Bellows] had done just that with a consumer router, corrupting the onboard NAND flash to the point where recovery via normal means was impossible. Armed with a working duplicate of the router, he wondered if the corrupted NAND flash could be substituted into the working router while it was running, and reflashed in place – and decided to find out.
Key to achieving the hack was finding a way to remove the existing NAND flash in the working router without crashing the system while doing so. This required careful disconnection of the chip’s power lines once the router had booted up, as well as tying the “Ready/Busy” and “Read Enable” pins to ground. With this done, the chip could carefully be removed with a hot air tool without disrupting the router’s operation. The new chip could then be soldered in place, and flashed with factory firmware via the router’s web interface. At this point, it could be powered down and the chips swapped normally back into their own respective routers, restoring both to full functionality.
It’s a neat hack, and one that shows that it’s sometimes worth taking a punt on your crazy ideas just to see what you can pull off. It also pays to know the deeper secrets of the hardware you run on your own home network.
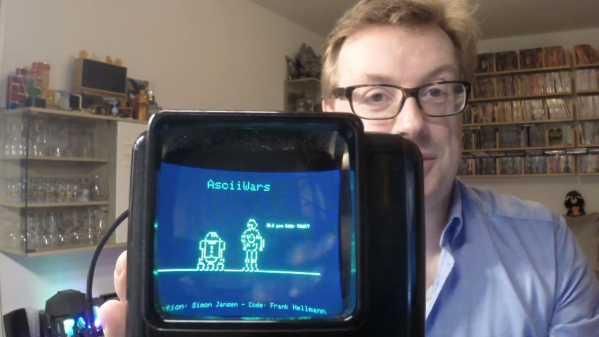
Enjoy An ASCII Version Of Star Wars In The Palm Of Your Hand For May The 4th
Everyone by now has probably seen the original — and best; fight us — installment of the Star Wars franchise, and likely the ASCII-art animation version of it that improves greatly on the film by eliminating all those distracting special effects, human actors, and the soundtrack. But what we haven’t had until now is a portable player for ASCIIWars, to enjoy the film in all its character-based glory while you’re on the go.
While this tribute to [Simon Jansen]’s amazing ASCII-art achievement might seem like a simple repackaging of the original, [Frank] actually had to go to some lengths to make this work. After getting [Simon]’s blessing, the build started with a WEMOS D1 Mini, a good platform for the project less for its wireless capabilities and more for its 4 MB of flash memory. A 240×360 TFT LCD display was selected to show the film; the scale of the display made most fonts hard to read, so [Frank] used Picopixel, a font designed for legibility on small screens. The animation file is stored on the SPIFFS file system on the D1’s flash memory, and a few lines of code parse it and send it to the display. The final touch is mounting the whole thing is an old slide viewer, which magnifies the display to make it a little easier to see.
As much as we applaud [Frank]’s tribute to [Simon]’s effort, there’s no reason to confine this to the Star Wars universe. If you read up on the history of ASCII art, which goes surprisingly far back, you might be inspired to render another classic film in ASCIImation and put it on a viewer like this. ASCII-Metropolis, anyone?
Continue reading “Enjoy An ASCII Version Of Star Wars In The Palm Of Your Hand For May The 4th”
Removing Supervisor Passwords And Learning Python
When learning a new programming language, it’s best to have a goal in mind and work towards it. [Timo] thought it was about time to learn python, and he also had a project in mind: removing the BIOS supervisor password from his old Thinkpad. From there it was just a few keystrokes (and some soldering) and he was able to change the BIOS password of this black box from the outside.
The build utilizes a BeagleBone to communicate with the laptop’s EEPROM via the I2C bus. An oscilloscope also monitors the bus to look for a specific window every four-seconds when the computer is not accessing the bus. During that short period, the EEPROM can be read and written to. Once the window opens, the BeagleBone executes the Python script, which attempts to read the EEPROM and can also perform actions such as removing or changing the BIOS supervisor password.
Of course, tinkering with the EEPROM on a laptop has a high risk of bricking the device, and not all laptops use the same security measures or even memory addresses for things like this, so documentation and precision are key. Also, with Thinkpads of this vintage it’s possible to replace the firmware on these chips entirely with a FOSS version called libreboot, and even though the process is difficult, it’s definitely recommended.
Continue reading “Removing Supervisor Passwords And Learning Python”