[Afonso] picked up a cheap energy use monitor a few years back. He really like the data it displays about his home’s electricity, using a sensor to gather this info and a display that communicates with it wirelessly. But there is no option to log or dump the data. He set out to reverse engineer the wireless protocol in order to extend the use of the system. As the name of this column implies, he failed to get this working.
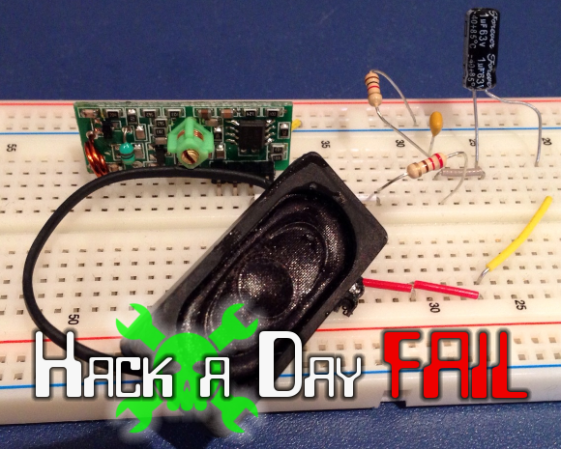
The hardware above is a 433Mhz transceiver that he rigged up as test hardware. It sounds like he’s assuming the monitor works on this band, which could have been his first misstep (we really don’t know). The speaker is there to give audible confirmation that he’s receiving something from the transmitter. This is where things start to get pretty weird. White noise was coming from the speaker, but when he stepped away from the bench it stopped. He was able to measure a regular pattern to the noise, and proceeded to place the speaker next to his computer MIC so that he could record a sample for further analysis.
Fail of the Week always aims to be a positive experience. In this case we’d like to have a conversation about the process itself. We agree that connecting a speaker (or headphones) should help get your foot in the door because your ear will recognize a rhythmic pattern when it is received. But with this noise, measuring the timing and recording a sample we’re not so sure about. Given the situation, how would you have soldiered on for the best chance at successfully sniffing out the communication scheme used by this hardware? Leave a comment below!
 Fail of the Week is a Hackaday column which runs every Wednesday. Help keep the fun rolling by writing about your past failures and sending us a link to the story — or sending in links to fail write ups you find in your Internet travels.
Fail of the Week is a Hackaday column which runs every Wednesday. Help keep the fun rolling by writing about your past failures and sending us a link to the story — or sending in links to fail write ups you find in your Internet travels.