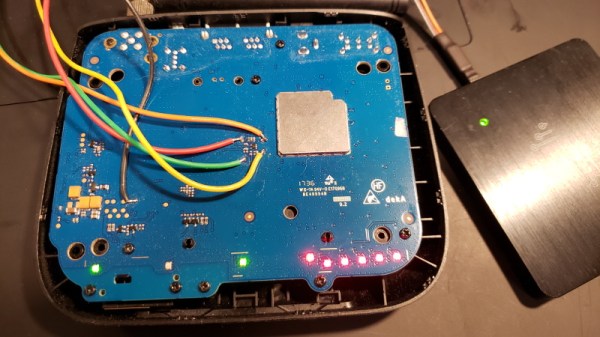
For most people, a battery pack that’s misbehaving simply means it’s time to get a new battery. But when the battery in their ThinkPad wasn’t able to muster up more than 20 minutes of runtime, [Shrinath Nimare] saw an opportunity to dig deeper and do a bit of investigating.
The problem seemed to be that the battery pack was reporting that it was 100% charged at just 11.7 V instead of the correct 12.3 V. As it turns out, that 11.7 V figure is only slightly above what the battery should be when its run flat — so in reality, the battery was never actually getting a charge and would report that it was dead after just a few minutes of use. But why?
With a logic analyzer attached to the pins of the battery, [Shrinath] set out to sniff its communications with the ThinkPad. Even if it wouldn’t lead to fixing the battery pack, the information obtained would potentially be useful for other projects, such as creating a custom high-capacity LiFePO4 pack down the line.
Continue reading “Sniffing Around Inside A ThinkPad Battery”