Some people state that ESP8266 is tolerant of 5 V logic levels on its GPIOs, while others vehemently disagree, pointing at the datasheet-stated 3.6 V maximum. Datasheets aren’t source code for compiling the chip, however, and aren’t universally correct and complete either. [Avian] decided to dig deeper into the claims, conduct an experiment with an actual ESP8266 chip, then share the results for all of us.
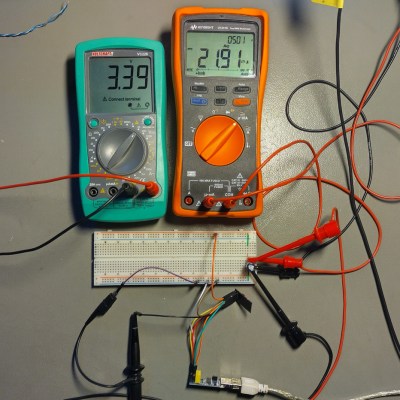
For the experiment, he used a curve tracer – a device capable of producing a wide range of voltages and measuring the current being consumed, then plotting the voltage-to-current relationship. This helps characterize all sorts of variables, from diode breakdown voltages to transistor characteristics. The curve tracer he uses is a capable and professional-looking DIY build of his, and arguably, deserves a separate write-up!
The reasoning behind [Avian]’s experiment is simple – if the pin, set to an input, starts consuming a higher amount of current at a certain voltage threshold, then there’s gotta be some chip-internal structure, intended or unintended, that would be damaged at this voltage. Curve tracer in hand, he set up an ESP-01 module to set a GPIO to input, and started increasing the voltage.
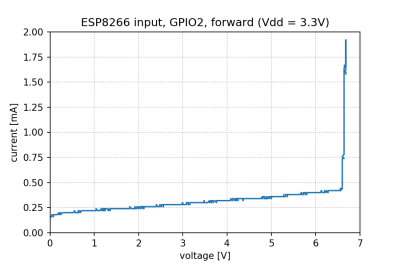
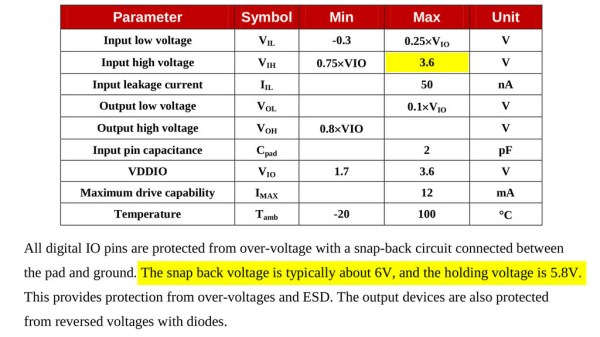
The tests have shown that, while there’s a reverse biased ESD diode from GPIO pins to ground, there don’t seem to be diodes from the GPIO pin to the VCC rail – and those are the primary concern for 5 V tolerance. There does seem to be something functionally akin to a 6 V Zener diode internally, which should clamp the voltage before it gets too way high for the chip to handle. None of that should be a problem for 5 V compatibility, and it seems fair to interpret this as a confirmation of 5 V tolerance until someone shows otherwise.
[Avian] didn’t want to destroy an ESP8266, so the experiment was conducted with a 1 K series resistor between the curve tracer and the input – which might have biased the results a bit. On the other hand, adding series resistors in front of your inputs is an overall underappreciated practice, 5 V or otherwise. He also points out that, while the pins don’t seem to be adversely impacted by the higher input voltage, the bootloader might set some of them to 3.3 V outputs on boot-up, shorting your 5 V source to your 3.3 V rail — worth keeping in mind!
[Avian]’s research journeys are fun to follow, and we recommend you check his blog out; last time, we covered his research of an innocent-looking 3.5 mm jack hiding a devious audio compensation circuit. Since we first covered the ESP8266 in 2014, we’ve been researching all the things it’s really capable of, and we brought up the topic of GPIO 5 V compatibility way back in 2016 – it’s reassuring to finally put this question to rest!
We thank [Adrian] for sharing this with us!