In some ways, we’ve become a little jaded when it comes to news from Mars, which almost always has to do with the Ingenuity helicopter completing yet another successful flight. And so it was with the report of flight number 54 — almost. It turns out that the previous flight, which was conducted on July 22, suffered a glitch that cut the flight short by forcing an immediate landing. We had either completely missed that in the news, or NASA wasn’t forthcoming with the news, perhaps until they knew more. But the details of the error are interesting and appear related to a glitch that happened 46 flights before, way back in May of 2021, that involves dropped frames from the video coming from the helicopter’s down-facing navigational camera. When this first cropped up back on flight six, it was only a couple of missed frames that nearly crashed the craft, thanks to confusion between the video stream and the inertial data. Flight engineers updated the aircraft’s software to allow for a little more flexibility with dropped frames, which worked perfectly up until the aborted flight 53.
exploit69 Articles
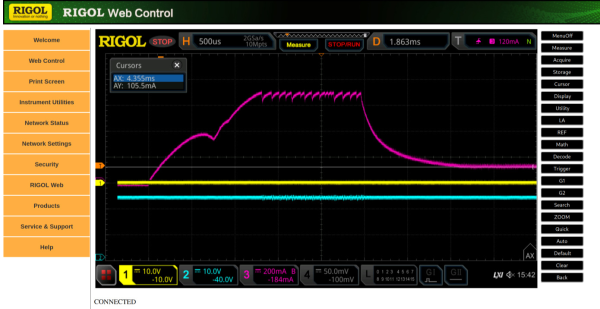
Remote Code Execution On An Oscilloscope
There are a huge number of products available in the modern world that come with network connectivity now, when perhaps they might be better off with out it. Kitchen appliances like refrigerators are the classic example, but things like lightbulbs, toys, thermostats, and door locks can all be found with some sort of Internet connectivity. Perhaps for the worse, too, if the security of these devices isn’t taken seriously, as they can all be vectors for attacks. Even things like this Rigol oscilloscope and its companion web app can be targets.
The vulnerability for this oscilloscope starts with an analysis of the firmware, which includes the web control application. To prevent potentially bricking a real oscilloscope, this firmware was emulated using QEMU. The vulnerability exists in the part of the code which involves changing the password, where an attacker can bypass authentication by injecting commands into the password fields. In the end, the only thing that needs to be done to gain arbitrary code execution on the oscilloscope is to issue a curl command directed at the oscilloscope.
In the end, [Maunel] suggests not connecting this oscilloscope to the Internet at all. He has informed the producer about it but as of this writing there has not been a resolution. It does, however, demonstrate the vulnerabilities that can be present in network-connected devices where the developers of the software haven’t gone to the lengths required to properly secure them for use with the modern Internet. Even things not connected to a traditional Internet connection can be targets for attacks.
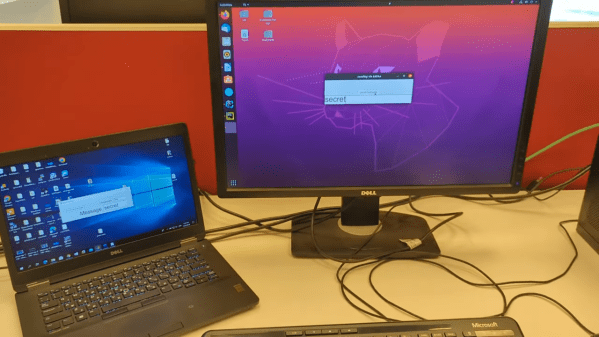
Exploring The Anatomy Of A Linux Kernel Exploit
A lot of talk and discussion happens anytime a hardware manufacturer releases a new line of faster, more powerful, or more efficient computers. It’s easy to see better and better specifications and assume that’s where all the progress is made. But without improved software and algorithms, often the full potential of the hardware can’t be realized. That’s the reason for the creation of io_uring, an improved system call interface in the Linux kernel. It’s also where [chompie] went to look for exploits.
The reason for looking here, in a part of the kernel [chompie] had only recently learned about, was twofold. First, because it’s a place where user space applications interact with the kernel, and second because it’s relatively new and that means more opportunities to find bugs. The exploit involves taking advantage of a complicated asynchronous buffer system, specifically at a location where the code confuses a memory location being used by the kernel with one which is supposed to be used for user space.
To actually get this to work as an exploit, though, a much more involved process is needed to make sure the manipulation of these memory addresses results in something actually useful, but it is eventually used to gain local privilege escalation. More about it can be found in this bug report as well. Thanks to the fact that Linux is open-source, this bug can quickly be fixed and the patch rolled out to prevent malicious attackers from exploiting it. Open-source software has plenty of other benefits besides being inherently more secure, though.
Breaking Into The Nintendo DSi Through The (Browser) Window
The Nintendo DSi was surpassed by newer and better handhelds many years ago, but that doesn’t stop people like [Nathan Farlow] from attempting to break into the old abandoned house through a rather unexpected place: the (browser) window.
When the Nintendo DSi was released in 2008, one of its notable features was a built-in version of the Opera 9.50 web browser. [Nathan] reasoned an exploit in this browser would be an ideal entry point, as there’s no OS or kernel to get past — once you get execution, you control the system. To put this plan into action, he put together two great ideas. First he used the WebKit layout tests to get the browser into weird edge cases, and then tracked down an Windows build of Opera 9.50 that he could run on his system under WINE. This allowed him to identify the use-after-free bugs that he was looking for.
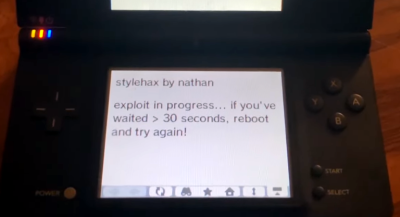 Now that he had an address to jump to, he just had to get his code into the right spot. For this he employed what’s known as a NOP sled; basically a long list of commands that do nothing, which if jumped into, will slide into his exploit code. In modern browsers a good way to allocate a chunk of memory and fill it would be a Float32Array, but since this is a 2008 browser, a smattering of RGBA canvases will do.
Now that he had an address to jump to, he just had to get his code into the right spot. For this he employed what’s known as a NOP sled; basically a long list of commands that do nothing, which if jumped into, will slide into his exploit code. In modern browsers a good way to allocate a chunk of memory and fill it would be a Float32Array, but since this is a 2008 browser, a smattering of RGBA canvases will do.
The actual payload is designed to execute a boot.nds file from the SD card, such as a homebrew launcher. If you want to give it a shot on your own DSi, all you need to do is point the system’s browser to stylehax.net.
If you’re looking for a more exotic way to crack into a DSi, perhaps this EM glitching attack might tickle your fancy?
Continue reading “Breaking Into The Nintendo DSi Through The (Browser) Window”
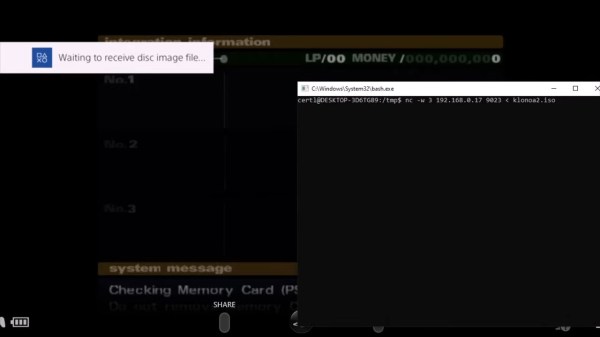
Subverting PS4 And PS5 Through The PS2 Emulator
Game console hacking remains a fascinating area, and we’re glad when someone brings the spoils of exploration for us to marvel at. This time, we’re looking at the [mast1c0re] hack story by [cturt] – an effort to find bugs in PS2 emulation toolkit present on Sony PlayStation 4 and 5 consoles, proving fruitful in the end. What’s more, this exploit seems unpatchable – not technically, but under the Sony’s security practices, this emulator falls under the category of things they refuse to patch when identified.
In this story, we’re taken on a journey through the PS2 emulator internals, going through known-exploitable PS2 games and learning about a prospective entry point. Circling around it, collecting primitives and gadgets, bypassing ASLR on the way there, the emulator is eventually escaped, with a trove of insights shared along the way. As a demonstration, [cturt] successfully loaded a different PS2 game from outside the PS2 emulator, transferring it to the PS4 over WiFi! Continue reading “Subverting PS4 And PS5 Through The PS2 Emulator”
Hackaday Links: August 21, 2022
As side-channel attacks go, it’s one of the weirder ones we’ve heard of. But the tech news was filled with stories this week about how Janet Jackson’s “Rhythm Nation” is actually a form of cyberattack. It sounds a little hinky, but apparently this is an old vulnerability, as it was first noticed back in the days when laptops commonly had 5400-RPM hard drives. The vulnerability surfaced when the video for that particular ditty was played on a laptop, which would promptly crash. Nearby laptops of the same kind would also be affected, suggesting that whatever was crashing the machine wasn’t software related. As it turns out, some frequencies in the song were causing resonant vibrations in the drive. It’s not clear if anyone at the time asked the important questions, like exactly which part of the song was responsible or what the failure mode was on the drive. We’ll just take a guess and say that it was the drive heads popping and locking.
SATAn Turns Hard Drive Cable Into Antenna To Defeat Air-Gapped Security
It seems like [Mordechai Guri]’s lab at Ben-Gurion University is the place where air-gapped computers go to die, or at least to give up their secrets. And this hack using a computer’s SATA cable as an antenna to exfiltrate data is another example of just how many side-channel attacks the typical PC makes available.
The exploit, deliciously designated “SATAn,” relies on the fact that the SATA 3.0 interface used in many computers has a bandwidth of 6.0 Gb/s, meaning that manipulating the computer’s IO would make it possible to transmit data from an air-gapped machine at around 6 GHz. It’s a complicated exploit, of course, and involves placing a transmitting program on the target machine using the usual methods, such as phishing or zero-day exploits. Once in place, the transmitting program uses a combination of read and write operations on the SATA disk to generate RF signals that encode the data to be exfiltrated, with the data lines inside the SATA cable acting as antennae.
SATAn is shown in action in the video below. It takes a while to transmit just a few bytes of data, and the range is less than a meter, but that could be enough for the exploit to succeed. The test setup uses an SDR — specifically, an ADALM PLUTO — and a laptop, but you can easily imagine a much smaller package being built for a stealthy walk-by style attack. [Mordechai] also offers a potential countermeasure for SATAn, which basically thrashes the hard drive to generate RF noise to mask any generated signals.
While probably limited in its practical applications, SATAn is an interesting side-channel attack to add to [Dr. Guri]’s list of exploits. From optical exfiltration using security cameras to turning power supplies into speakers, the vulnerabilities just keep piling up.
Continue reading “SATAn Turns Hard Drive Cable Into Antenna To Defeat Air-Gapped Security”