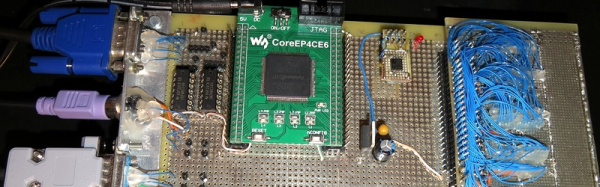
The 1 kB Challenge deadline has come and gone. The judges have done their work, and we’re ready to announce the winners. Before you jump down to find out who won, I’d like to take a moment to say thanks to everyone who participated. We had some incredible entries. To say that judging was hard is quite an understatement. Even [Eben Upton], father of the Raspberry Pi got in on the action. He created a new helicopter game for the classic BBC Micro. Look for writeups on the winners and many of the other entries in the coming weeks.
Grand Prize
 The grand prize goes to [Jaromir Sukuba] for Brainf*cktor. [Jaromir] went above and beyond this time. He created a computer which can be programmed in everyone’s favorite esoteric programming language. Brainf*cktor uses 1019 bytes of program memory in [Jaromir’s] PIC18F26K22. You can write, execute and edit programs. [Jaromir] ran into a bit of a problem with his LCD. The character tables would have thrown him over the 1 kB limit. Not a problem – he designed his own compressed character set, which is included in the 1019 bytes mentioned above. All the clever software takes physical form with a homemade PCB, and a case built from blank PCB material. Best of all, [Jaromir] has explained his software tricks, as well as included a full build log for anyone who wants to replicate his project. All that hard work will be rewarded with a Digi-Comp II kit from EMSL.
The grand prize goes to [Jaromir Sukuba] for Brainf*cktor. [Jaromir] went above and beyond this time. He created a computer which can be programmed in everyone’s favorite esoteric programming language. Brainf*cktor uses 1019 bytes of program memory in [Jaromir’s] PIC18F26K22. You can write, execute and edit programs. [Jaromir] ran into a bit of a problem with his LCD. The character tables would have thrown him over the 1 kB limit. Not a problem – he designed his own compressed character set, which is included in the 1019 bytes mentioned above. All the clever software takes physical form with a homemade PCB, and a case built from blank PCB material. Best of all, [Jaromir] has explained his software tricks, as well as included a full build log for anyone who wants to replicate his project. All that hard work will be rewarded with a Digi-Comp II kit from EMSL.
First Prize
 First prize goes to [Dumitru Stama] with M0S – CortexM0 RTOS in 1024 bytes. Operating systems are complex beasts. Many of our readers have toyed with the Linux Kernel. But writing a real-time OS from scratch? That’s quite an undertaking. [Dumitru] didn’t shy away from the challenge. He designed a Real-Time Operating System (RTOS) for ARM processors, written completely in ARM thumb assembly instructions. This is no bare-bones executive. M0S has a rich list of features, including preemptive task scheduling, mutexes, and inter-process communication. [Dumitru] even gave us memory allocation with an implementation of malloc() and free(). The OS was demonstrated with a NUCLEO-F072RB board from ST-Micro.
First prize goes to [Dumitru Stama] with M0S – CortexM0 RTOS in 1024 bytes. Operating systems are complex beasts. Many of our readers have toyed with the Linux Kernel. But writing a real-time OS from scratch? That’s quite an undertaking. [Dumitru] didn’t shy away from the challenge. He designed a Real-Time Operating System (RTOS) for ARM processors, written completely in ARM thumb assembly instructions. This is no bare-bones executive. M0S has a rich list of features, including preemptive task scheduling, mutexes, and inter-process communication. [Dumitru] even gave us memory allocation with an implementation of malloc() and free(). The OS was demonstrated with a NUCLEO-F072RB board from ST-Micro.
[Dumitru] didn’t just drop a GitHub link and run. He documented M0S with seven project logs and a 37-minute long video. The video uses electronic whiteboard drawings to clearly explain all the internal workings of the operating system, as well as how to use it.
[Dumitru] is the proud new owner of a Maker Select 3D printer V2!
Second Prize
 Second prize goes to [Cyrille Gindreau] with 1K Challange Laser. Vector lasers generally take lots of memory. You have to manage galvanometers, laser drive, and perform all the magic it takes to convert a set of vectors to lines drawn in space. The project uses 912 bytes of program and initialized data memory to command an MSP430 to draw an image.
Second prize goes to [Cyrille Gindreau] with 1K Challange Laser. Vector lasers generally take lots of memory. You have to manage galvanometers, laser drive, and perform all the magic it takes to convert a set of vectors to lines drawn in space. The project uses 912 bytes of program and initialized data memory to command an MSP430 to draw an image.
Proving that flattery will get you everywhere, [Cyrille] picked the Hackaday logo as the subject. The Jolly Wrencher is not exactly simple to convert to vector format, though. It took some careful optimizations to come up with an image that fit within 1 kB. [Cyrille] wins a Bulbdial Clock kit from EMSL.
Third Prize
 Third prize goes to [Mark Sherman] with tinygames. Video games have been around for awhile, but they are never quite this small. [Mark] coaxed the minuscule Atmel ATtiny84 to play Centipede with only 1024 bytes of program memory. Even the BOM is kept small, with just a few support components. Control is handled by an Atari 2600 compatible joystick. Video is black and white NTSC, which is demonstrated on a period accurate CRT. [Mark] generates his video by racing the electron beam, exactly the same way the Atari 2600 did it.
Third prize goes to [Mark Sherman] with tinygames. Video games have been around for awhile, but they are never quite this small. [Mark] coaxed the minuscule Atmel ATtiny84 to play Centipede with only 1024 bytes of program memory. Even the BOM is kept small, with just a few support components. Control is handled by an Atari 2600 compatible joystick. Video is black and white NTSC, which is demonstrated on a period accurate CRT. [Mark] generates his video by racing the electron beam, exactly the same way the Atari 2600 did it.
[Mark] will take home a Blinkytile kit from Blinkinlabs.
Final thoughts
First of all, I’d like to thank the judges. Our own [Jenny List], [Gerrit Coetzee], [Pedro Umbelino], [Bil Herd], and [Brian Benchoff] worked hard with me in judging this contest. I’d also like to thank our community for creating some amazing projects. The contest may be over, but these projects are now out there for others to build, enjoy, and learn from.
I’ve wanted to organize this contest since [Jeri Ellsworth] and [Chris Gammell] took on the 555 contest way back in 2011. The problem is creating a set of rules that would be relatively fair to every architecture. I think 133 entries to this contest proves that we found a very fair set of constraints. It is safe to say this won’t be the last 1 kB Challenge here at Hackaday, so if you have ideas for future editions, share them in the comments!






 The grand prize goes to [Jaromir Sukuba] for
The grand prize goes to [Jaromir Sukuba] for  First prize goes to [Dumitru Stama] with
First prize goes to [Dumitru Stama] with  Second prize goes to [Cyrille Gindreau] with
Second prize goes to [Cyrille Gindreau] with  Third prize goes to [Mark Sherman] with
Third prize goes to [Mark Sherman] with