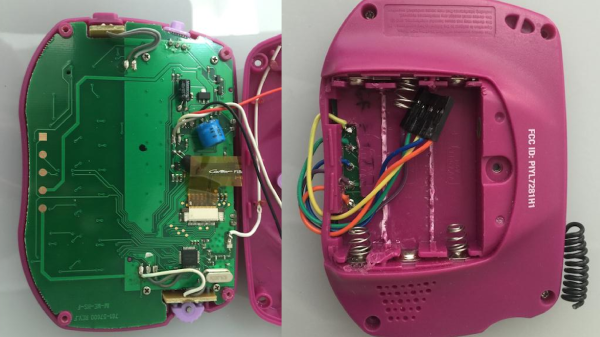
If you have a wireless controlled garage door, a child’s toy can wirelessly open it in a few seconds. [Samy Kamkar] is a security researcher who likes to”think bad, do good”. He’s built OpenSesame, a device that can wirelessly open virtually any fixed-code garage door in seconds, exploiting a new attack he’s discovered in wireless fixed-pin devices, using the Mattel IM-ME toy.
The exploit works only on a gate or garage which uses “fixed codes”. To prevent this type of attack, all you need to do is to upgrade to a system which uses rolling codes, hopping codes, Security+ or Intellicode. These are not foolproof from attack, but do prevent the OpenSesame attack along with other traditional brute forcing attacks. It seems there are at least a couple of vendors who still have such vulnerable products, as well as several more whose older versions are affected too.
Before you read further, a caveat – the code released by [Samy] is intentionally bricked to prevent it from being abused. It might work, but just not quite. If you are an expert in RF and microcontrollers, you could fix it, but then you wouldn’t need his help in the first place, would you?
The IM-ME is a defunct toy and Mattel no longer produces it, but it can be snagged from Amazon or eBay if you’re lucky. The Radica Girltech IM-ME texting toy has been extensively hacked and documented. Not surprising, since it sports a TI CC1110 sub-GHz RF chip, an LCD display, keyboard, backlight, and more. A good start point is the GoodFET open-source JTAG adapter, followed by the work of [Travis Godspeed] , [Dave] and [Michael Ossmann].
One issue with fixed code systems is their limited key space. For example, a remote with 12 binary dip switches supports 12 bits of possible combinations. Since its binary and 12 bits long, that’s 2^12, which is 4096 possible combinations. With a bit of math, [Samy] shows that it takes 29 minutes to open an (8-12)-bit garage, assuming you know the frequency and baud rate, both of which are pretty common. If you have to attempt a few different frequencies and baud rates, then the time it takes is a multiple of 29 minutes. If you don’t transmit the codes multiple times, and remove the pauses in between codes, the whole exercise can be completed in 3 minutes.
The weak link in the hardware is how the shift registers which decode the received codes work. Each bit is loaded in the register sequentially, gradually moving as additional bits come in and push the previous ones. This, and using an algorithm [Samy] wrote based on the De Bruijn sequence, the whole brute force attack can be completed in just over 8 seconds. OpenSesame implements this algorithm to produce every possible overlapping sequence of 8-12 bits in the least amount of time.
You can take a look at understanding how the code works by checking it out on Github. [Samy] loves doing such investigative work – check out his combo lock code breaker we featured recently, the scary, keyboard sniffing wall wart and the SkyJack – a drone to hack all drones.
Continue reading “Hacking The IM-ME To Open Garages” →