Schools are closed here in Germany until after Easter vacation, and that means that our almost-six-year-old son Max is staying at home with us. The good news is that my wife and I work from home anyway, so it’s not too stressful as long as he can look after himself for eight hours per day. The bad news is that there’s no way a kindergarten kid can take care of himself for such long stretches, and we don’t want to just park him in front of the boob tube. At least there’s two of us.
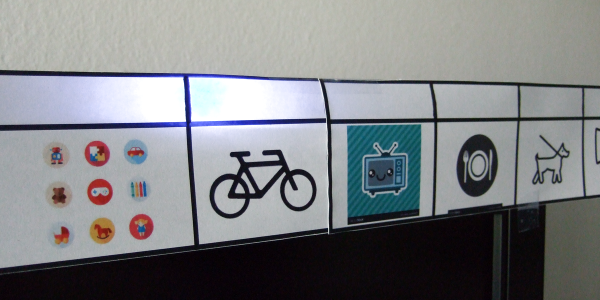
The new stay-at-home life has required some adjustment, but for at least the first five days (and counting) it’s working out pretty darn well. One trick: my wife came up with the idea of a visual schedule to help Max divide his day up into kindergarten-sized chunks, and then we added an LED strip behind it to turn it into a linear clock of sorts. And we did it with stuff we had lying around the house.
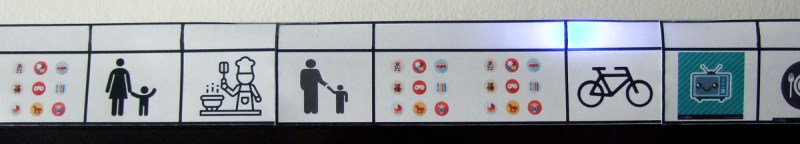
Granted, it’s not a super deep hacky-hack, and some of you out there could probably get it done with a handful of 555 timers. But it was quick, gets the job done, and heck, with NTP sync, it’s the most accurate kiddie clock in the world! So those of you out there who are stuck like we are, trying to balance childcare and working from home, here’s a quick project that can increase familial harmony while giving you an excuse to order more LED strips.