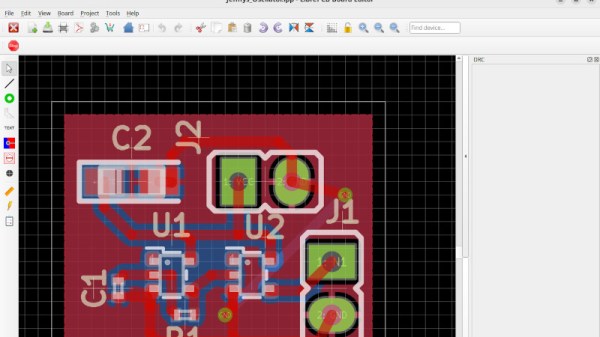
Nearly three years ago at the start of 2020 and before the pandemic hit, we took a look at an up-and-coming player in the world of PCB design. LibrePCB is by no means as old as the more established players, but at the time it was joining the ranks of open-source EDA packages with its first early stable releases. It showed a lot of promise but was still a little rough around the edges back then, but in the years since it’s advanced to the extent that in September they released version 1.0. That’s a significant moment for any open source package, so it’s time to return and take another look. It’s a cross-platform package with builds available for Linux, Windows, MacOS and FreeBSD, of which I needed the Linux version. There are one or two options to choose from, I went for the appImage as probably the least trouble. Very quickly I was in a new EDA package, and I set out to make a simple Schmitt trigger oscillator as a test project. Continue reading “Review: LibrePCB Hits Version 1.0”
Metamaterial Enables Topological Pumping Of Elastic Surface Waves
Although it is generally assumed that surface elastic waves (vibrations) — such as those of earthquakes — will travel mostly unimpeded until their energy dissipates, there are ways to ‘steer’ this energy using metamaterials.
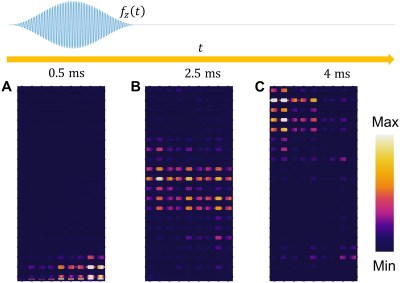
(A to C). The magnitude of total displacement field at 0.5 ms, 2.5 ms, and 4 ms, respectively. A 50-cycle tone burst signal centered at 41.88 kHz is simulated on the bottom supercell. (Wang et al., 2023)
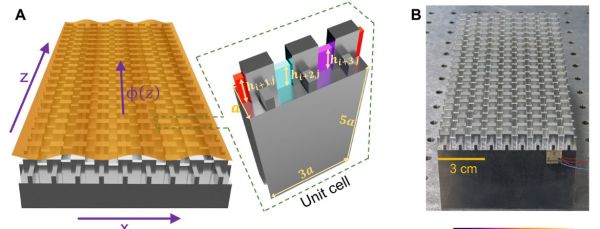
A recent study by [Shaoyun Wang] and colleagues in Science Advances details how a carefully modelled grouping of columns creates what is termed a synthetic dimension. In their experimental setup, it is demonstrated how an applied wave is guided across the metamaterial, rather than spreading out the way which we would expect to see in conventional materials.
Interestingly, in the paper it is also demonstrated how the same technique can be used to create a wave-splitter that diverts the wave energy in two distinct directions. Due to the innate resistance of this type of structure to defects, manufacturing it is not too complicated.
In this experiment the metamaterials were milled out of a block of aluminium on a CNC mill, which makes it seem eminently realistic that it could be scaled up and translated to other applications. Conceivably annoyances like vibrations from road traffic and heavy machinery, all the way up to the destructive energies of earthquakes could one day be reduced, redirected or even extinguished using structures as demonstrated here.
Chip Shortage Engineering: Misusing DIP Packages
After years of seeing people showing off and trading their badge Simple Add-Ons (SAOs) at Supercon, this year I finally decided to make one myself. Now for a first attempt, it would have been enough to come up with some cool PCB art and stick a few LEDs on it. But naturally I started with a concept that was far more ambitious than necessary, and before long, had convinced myself that the only way to do the thing justice was to have an onboard microcontroller.
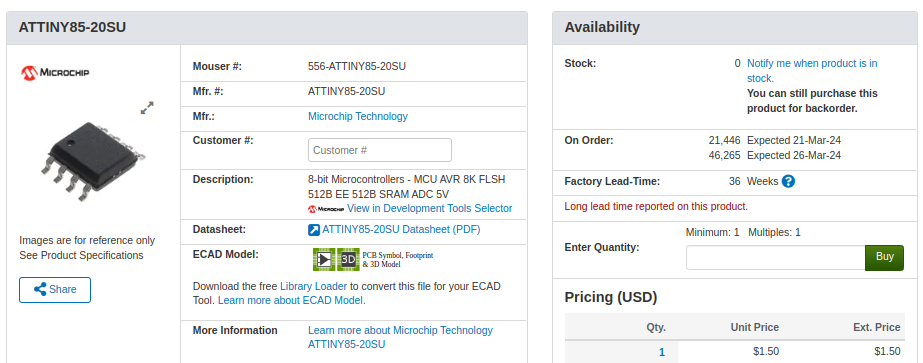
My first thought was to go with the venerable ATtiny85, and since I already had a considerable stock of the classic eight-pin DIP MCUs on hand, that’s what I started prototyping with. After I had something working on the breadboard, the plan was to switch over to the SOIC-8 version of the chip which would be far more appropriate for something as small as an SAO.
Unfortunately, that’s where things got tricky. I quickly found that none of the major players actually had the SMD version of the chip in stock. Both DigiKey and Mouser said they didn’t expect to get more in until early 2024, and while Arrow briefly showed around 3,000 on hand, they were all gone by the time I checked back. But that was only half the problem — even if they had them, $1.50 a piece seems a hell of a lot of money for an 8-bit MCU with 8K of flash in 2023.
The whole thing was made all the more frustrating by the pile of DIP8 ATtiny85s sitting on the bench, mocking me. Under normal circumstances, using them in an SAO wouldn’t really be a problem, but eight hand-soldered leads popping through the front artwork would screw up the look I had in mind.
While brooding over the situation my eyes happened to fall on one of the chips I had been fiddling with, it’s legs badly bent from repeated trips through the programmer. Suddenly it occurred to me that maybe there was a way to use the parts I already had…
Continue reading “Chip Shortage Engineering: Misusing DIP Packages”
At Last! Faster OpenSCAD Rendering Is On The Horizon
Known as “The Programmers Solid 3D CAD Modeller”, OpenSCAD is used by many people for whom writing code comes more naturally than learning a fiddly user interface. It’s a very capable piece of software, but regular users will tell you that it can be rather slow when it comes to rendering your work. We’re very pleased to see that a fix for this has been produced courtesy of [@ochafik], can now be found as an experimental feature in nightly builds, and will in due course no doubt find its way to official releases.
Despite a modern computer invariably having a multi-core architecture, it might surprise you to find that OpenSCAD wasn’t able to take advantage of this previously. The above-linked thread spans over a decade of experimenting and contains some fascinating discussions if you’re prepared to wade through it, and culminates a few weeks ago in the announcement of the new feature giving access to multiple CPUs. We don’t have it yet, but it’s great to know it’s in the works and we’re looking forward to render time involving considerably less of a wait.
So many OpenSCAD projects have passed through these pages over the years, it’s safe to say that it has a significant user base among Hackaday readers. It’s still something an AI hasn’t mastered yet though.
Thanks [pca006132] for the tip.
Femtosecond Laser Clones Itself In Glass
When researchers at the Galatea laboratory in Switzerland set out to create a femtosecond laser in glass they weren’t certain it was going to work. To be precise, their goal was to create a femtosecond laser cavity using carefully aligned optics. Rather than using the traditional, discrete method, they used a commercial femtosecond laser to carve out the elements of the optical cavity in glass. The choice for glass came down to the low thermal expansion of this material, and it being transparent for the optical frequencies being targeted.
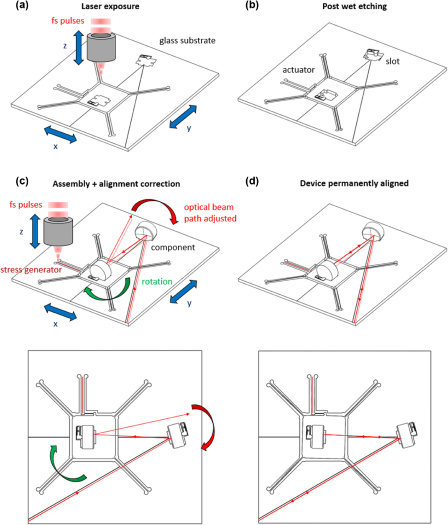
Even after using the existing laser to create the rough laser cavity, the resulting optical mirrors were not aligned properly, but this was all part of the plan.
By also adding slots that created a flexure mechanism, brief laser pulses could be used to gradually adjust the mirrors to create the perfect alignment. During subsequent testing of the newly created laser cavity it was found to be operating as expected. The original femtosecond laser had successfully created a new femtosecond laser.
Perhaps the most tantalizing aspect of this research is that this could enable much faster and ultimately cheaper production of such laser systems, especially once the tedious and currently completely manual mirror alignment procedure is automated. In addition, it raises the prospect of producing other types of optics including splitters and guides in a similar manner.
Computer Space Replica Is Up And Running
You never forget your first time — watching someone pour several quid’s worth of 10p pieces into a Space Invader machine in 1978, upsetting for a youngster who wanted to have a turn. We’re still waiting, but [Alston] has found an interesting way to get around those arcade video game hoggers by building a replica of Computer Space, the first commercial arcade video game.
Released in 1971, the groundbreaking game was designed by gaming legends [Nolan Bushnell] and [Ted Dabney], and came in a striking curvy fiberglass case that was molded by a manufacturer of swimming pools. [Alston] hasn’t built the case yet, but he does have the electronics up and running.
The electronics of Computer Space are interesting, because there is no microprocessor in there. Instead, it is built from discrete components. [Nolan] had originally planned to use a mini computer called the Data General Nova 800. However, he realized that he could make it cheaper by building it out of discrete components. As [Nolan] described it in an oral history at the Smithsonian [PDF link], the idea came to him after a post-Thanksgiving dinner nap:
“Screw the minicomputer. Get rid of it. Do it all in hardware. Make the game out of this collection, just make it a simple state machine. And the minute that happened, it was like knife through butter. Not only did I get the cost down, but what was budgeted for $1,500 worth of minicomputer, the whole damn computer cost me less than $300 in glue parts. So, I knew that I had something.”
That decision makes it an interesting project to build a replica. Although you can emulate it on a modern computer easily (there is even a version that runs in CSS in the browser). [Alston] is going the hard route, building replica PCBs and using the same components where possible, helped by people who have documented it. So far, the boards are and running and displaying a grainy, pixelated image on a portable TV.
The next step is to take the replica electronics box he has built and make a cabinet to put it into. That’s a big project, and [Alston] is looking for someone with an original cabinet that he can examine and document.
The Path To Profiling Extraterrestrial Atmospheres With Astrophotonics
A major part of finding extraterrestrial life is to be able to profile the atmosphere of any planets outside of our solar system. This is not an easy task, as these planets are usually found through the slight darkening of their star as they pass in front of it (transition). Although spectroscopy is the ideal way to profile the chemical composure of such a planet, having a massive, extremely bright star right next to the planet is more than enough to completely overpower the faint light reflecting off the planet’s surface and through its atmosphere. This is a major issue that the upcoming Habitable Exoplanet Imaging Mission (HabEx, also called the Habitable Worlds Observatory, or HWO) hopes to address using a range of technologies, including a coronagraph that should block out most of the stellar glare.
While this solves much of the issue, there are still a range of issues which the new field of astrophotonics seeks to address, as detailed in a recent paper by Nemanja Jovanovic and colleagues. This involves not only profiling chemical compositions, but also increasing the precision when monitoring for planet transit events using e.g. semiconductors-based laser frequency combs. These are generally combined with a spectral flattener, which in experimental on-chip form are significantly less bulky than previous setups, to the point where they don’t necessarily have to be Earth-based.
Continue reading “The Path To Profiling Extraterrestrial Atmospheres With Astrophotonics”