Longtime followers of [Ken Shirriff’s] work are accustomed to say asking “Where does he get such wonderful toys?”. This time around he’s laid bare the guidance computer from a Titan missile. To be specific, this is the computer that would have been found in the Titan II, an intercontinental ballistic missile that you may remember as a key part of the plot of the classic film WarGames. Yeah, those siloed nukes.
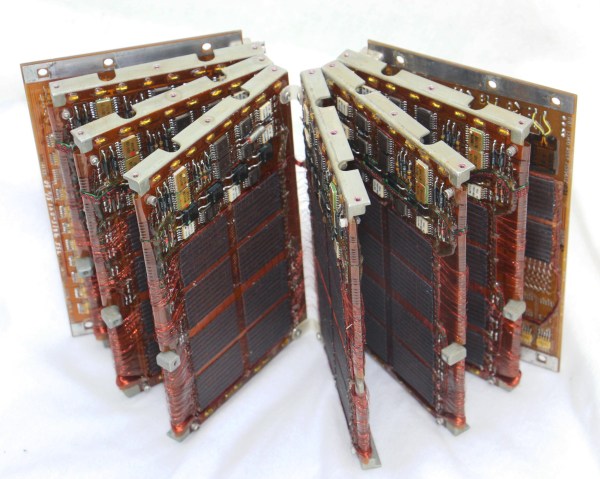
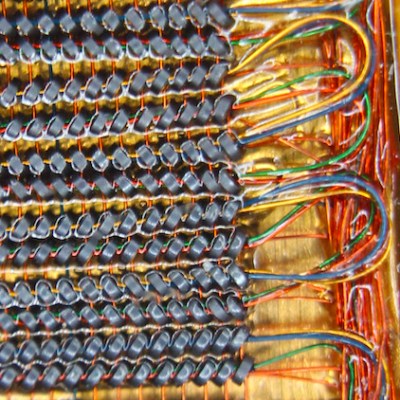 Amazingly these computers were composed of all digital logic, no centralized controller chip in this baby. That explains the need for the seven circuit boards which host a legion of logic chips, all slotting into a backplane.
Amazingly these computers were composed of all digital logic, no centralized controller chip in this baby. That explains the need for the seven circuit boards which host a legion of logic chips, all slotting into a backplane.
But it’s not the logic that’s mind-blowing, it’s the memory. Those dark rectangles on almost every board in the image at the top of the article are impressively-dense patches of magnetic core memory. That fanout is one of two core memory modules that are found in this computer. With twelve plates per module (each hosting two bits) plus a parity bit on an additional plate, words were composed of 25-bits and the computer’s two memory modules could store a total of 16k words.
This is 1970’s tech and it’s incredible to think that when connected to the accelerometers and gyros that made up the IMU this could use dead reckoning to travel to the other side of the globe. As always, [Ken] has done an incredible job of walking through all parts of the hardware during his teardown. He even includes the contextual elements of his analysis by sharing details of this moment in history near the end of his article.
If you want to geek out a little bit more about memory storage of yore, you can get a handle on core, drum, delay lines, and more in Al Williams’ primer.