PCB makers Dirty made a name for themselves in the prototype PCB biz, with a convenient web form and numerous options for PCB color, thickness, layers, silk screening, and so on. Now they’ve branched out into custom cabling with Dirty Cables.
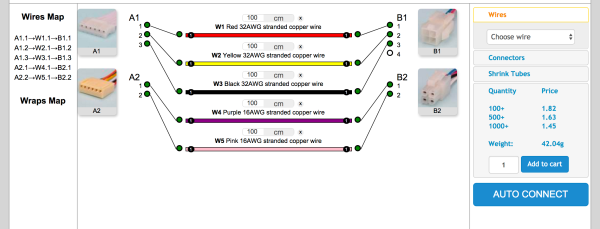
You can design it yourself by dragging wires and connectors out of a sidebar and arranging them on a workspace, deciding which wire goes to what pin of the connector. Your choices for wires include various gauges and ribbon configurations. You choose a color (they have eleven) select connectors and drag those out too–choose from 17 cable-to-cable and cable-to-board connector families. We made a quick cable with four 32ga wires and two 16ga wires, with two different connectors on each side, with pricing updated realtime. If you want a sample pack of connectors, Dirty sells them for $10.
The downside to the service: there’s a minimum order of 100, though paying Shenzhen prices might make it worth your while. Just imagining crimping all of those connectors makes Hackaday’s hands hurt.
To get a sense of the diversity of connectors out there, read Elliot’s piece on the connector zoo that we published last year.
[thanks, Akiba]