Chromecasts are fantastic little products, they’re basically little HDMI sticks you can plug into any monitor or TV, and then stream content using your phone or computer as the controller. They are powered by a micro USB port in the back, and if you’re lucky, your TV has a port you can suck the juice off. But what if you want to turn it off while you use a different input on your TV so that your monitor will auto-sleep? You might have to build a power switch.
 Now in all honesty, the Chromecast gets hot but the amount of power it draws when not in use is still pretty negligible compared to the draw of your TV. Every watt counts, and [Ilias] took this as an opportunity to refine his skills and combine a system using an Arduino, Bluetooth, and Android to create a robust power switch solution for the Chromecast.
Now in all honesty, the Chromecast gets hot but the amount of power it draws when not in use is still pretty negligible compared to the draw of your TV. Every watt counts, and [Ilias] took this as an opportunity to refine his skills and combine a system using an Arduino, Bluetooth, and Android to create a robust power switch solution for the Chromecast.
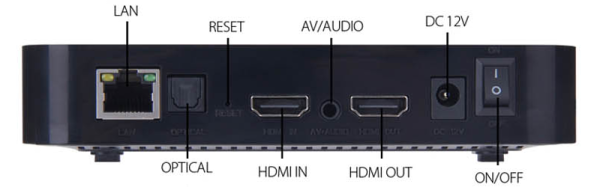
The setup is rather simple. An HC-05 Bluetooth module is connected to an Attiny85, with some transistors to control a 5V power output. The Arduino takes care of a bluetooth connection and uses a serial input to control the transistor output. Finally, this is all controlled by a Tasker plugin on the Android phone, which sends serial messages via Bluetooth.
All the information you’ll need to make one yourself is available at [Ilias’] GitHub repository. For more information on the Chromecast, why not check out our review from almost three years ago — it’s getting old!