Ah, the beloved Commodore 64. The “best-selling computer system of all time”. And hobbyists are keeping the dream alive, still producing software for it today. Which leads us to a problem with using such old equipment. When you get your copy of Petscii Robots on cassette, and try to fastload it, your machine might just consistently fail to load the program. That’s fine, time to pull out the cue-tips and rubbing alcohol, and give the read heads a good cleaning. But what if that doesn’t do the job? You may just have another problem, like tape speed drift.
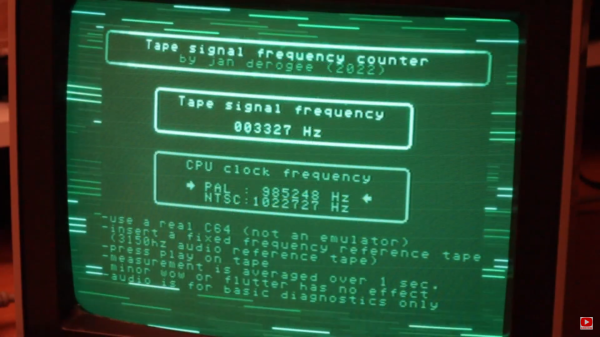
There are several different ways to measure the current tape speed, to dial it in properly. The best is probably a reference cassette with a known tone. Just connect your frequency counter or digital oscilloscope, and dial in the adjustment pot until your Datasette is producing the expected tone. Oh, you don’t have a frequency counter? Well good news, [Jan Derogee] has a solution for you. See, you already have your Datasette connected to a perfectly serviceable frequency counter — your Commodore computer. He’s put out a free program that counts the pulses coming from the Datasette in a second. So play a reference cassette, run the program, and dial in your Datasette deck. Simple! Stick around after the break for a very tongue-in-cheek demonstration of the problem and solution.
Continue reading “Commodore Datasette Does Its Own Calibration”






 The metal pads in question seem to be far too thin and structurally unsound, as one can readily spot, their cross-section is dwarfed by the cross-section of cables soldered to them. This would create a segment of increased resistance and heat loss, exacerbated by any flexing of the thick and unwieldy cabling. Due to the metal being so thin, the stress points seem quite flimsy, as one of the metal pads straight up broke off during disassembly of the connector.
The metal pads in question seem to be far too thin and structurally unsound, as one can readily spot, their cross-section is dwarfed by the cross-section of cables soldered to them. This would create a segment of increased resistance and heat loss, exacerbated by any flexing of the thick and unwieldy cabling. Due to the metal being so thin, the stress points seem quite flimsy, as one of the metal pads straight up broke off during disassembly of the connector.









