Getting into a big electronics project often involves the use of specialized tools, namely the use of some sort of soldering iron or other way to apply solder to often intricate, tiny, and heat-sensitive parts. While it’s best to learn to pick up this skill at some point, it’s not always necessary, even for big, complicated projects like [DerULF1]’s full 8-bit computer that he built entirely on breadboards.
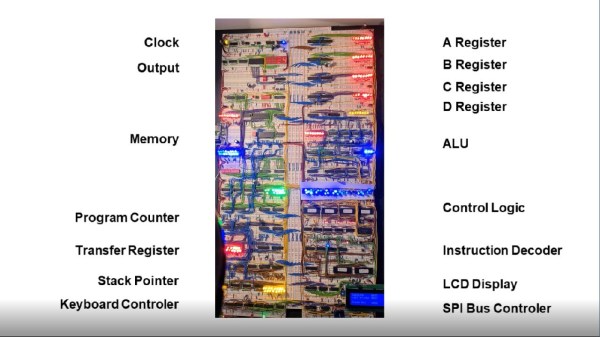
For a fully featured 8-bit computer, this build goes deep into the details of how the computer works. The clock allows programs to be stepped through one cycle at a time, and even the memory can be individually accessed with a set of switches. There are plenty of other interesting features as well, such as using registers to access extra memory. It features an SPI port and PS/2 keyboard controller and also loads programs from an SD card.
The build was inspired by some of [Ben Eater]’s projects which famously focus on using logic gates and TTL chips to perform complex tasks, such as another breadboard computer which plays snake on a small display. It’s certainly a great way to learn about the inner function of computers, and better still that no soldering is required. But you may need a few extra breadboards.