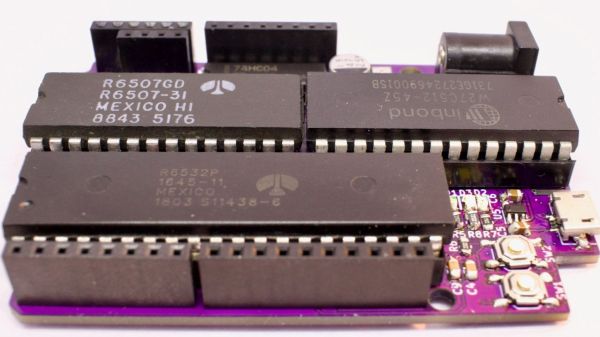
Back in 2020 in the brief lull between COVID lockdowns in the UK, I found myself abruptly on the move, with a very short time indeed to move my possessions into storage. As I was going through the accumulated electronic detritus of over four decades, I happened upon a grey box with some wires hanging out of it, and more than a few memories. This was a Sky VideoCrypt decoder, and the wires were part of the so-called “Season” interface to attach it to the serial port of a PC. It had this modification in the hope of catching some unauthorised free satellite TV, and in its day this particular hack caused some headaches for the broadcaster.
When More Than 4 Channels Was A Novelty

In the 1980s and early 1990s, there was very little in the way of digital broadcasting on either satellites or terrestrial networks, almost everything on TV was sent out as standard definition analogue video. The four terrestrial channels where I grew up were all free-to-air, and if you had a satellite dish you could point it at any one of a variety of satellites and receive more free-to-air channels if you didn’t mind most of them being in German. Premium satellite programming was encrypted though, either through a range of proprietary analogue schemes, or for the British broadcaster Sky’s offering, through their VideoCrypt system. This used a 64 kB buffer to store each line of video, and rotate it round any one of 256 points along its length, resulting in an unintelligible picture.
Sky was the UK’s big gorilla of premium broadcasters, a role they kept for many years, and which was only eroded by the advent of streaming services. As such they snapped up exclusive first access to much of the most desirable content of the day, restricting it to only their British pay-to-subscribe customers. A viewer in the UK who grumbled about Star Trek Next Generation not being on the BBC could at least cough up for Sky, but if they didn’t have a British address they were out of luck. It was in this commercial decision, whether it was based upon business or on licensing, that Sky unwittingly sowed the seeds of Videocrypt’s demise.
Continue reading “How Star Trek Breached The Defences Of A Major Broadcaster”