These days we’re surrounded by high-speed electronics and it’s no small feat that they can all play nicely in near proximity to each other. We have RF emissions standards to thank, which ensure new products don’t spew forth errant signals that would interfere with the data signals traveling through the ether. It’s long been the stuff of uber-expensive emissions testing labs, and failure to pass can leave you scratching your head. But as Alex Whittimore shows in this workshop from the 2020 Hackaday Remoticon, you can do a lot of RF emissions debugging with simple and inexpensive tools.
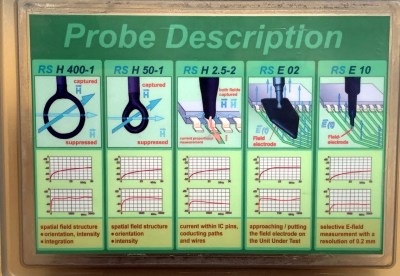
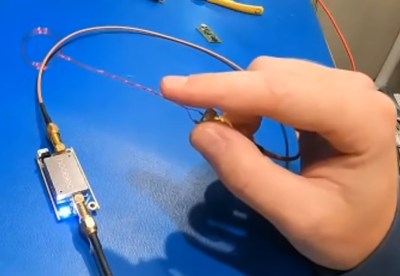
You can get a surprisingly clear picture of what kind of RF might be coming off of a product by probing it on your own workbench. Considering the cost of the labs performing FCC and other certifications, this is a necessary skill for anyone who is designing a product headed to market — and still damn interesting for everyone else. Here you can see two examples of the probes used in the process. Although one is a pack of professional tools and other is a bit of enameled wire (magnet wire), both are essentially the same: a loop of wire on which a magnetic field will induce a very small current. Add a Low-Noise Amplifier (LNA) and you’ll be up and measuring in no-time.
I really enjoyed how Alex started his demo with “The Right WayTM” of doing things — using a proper spectrum analyzer to visualize data from the probes. But the real interesting part is “The Hacker WayTM” which leverages an RTL-SDR dongle and some open-source software to get the same job done. Primarily that means using SDRAngel and QSpectrumAnalyzer which are both included in the DragonOS_LTS which can be run inside of a virtual machine.
Continue reading “Remoticon Video: Basics Of RF Emissions Debugging Workshop”