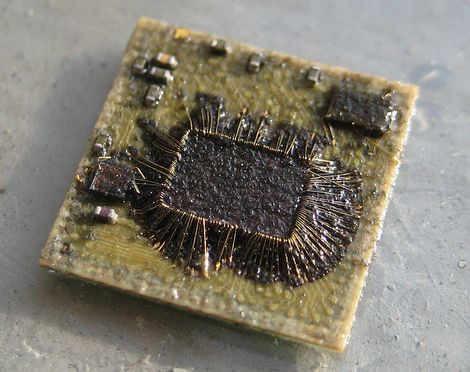
First introduced as an IC back in 1968, but with roots that go back to 1941, the 741 has been tweaked and optimized over the years and is arguably the canonical op-amp. [Ken Shirriff] decided to take a look inside everybody’s favorite op-amp, and ended up with some good-looking photomicrographs and a lot of background on the chip.
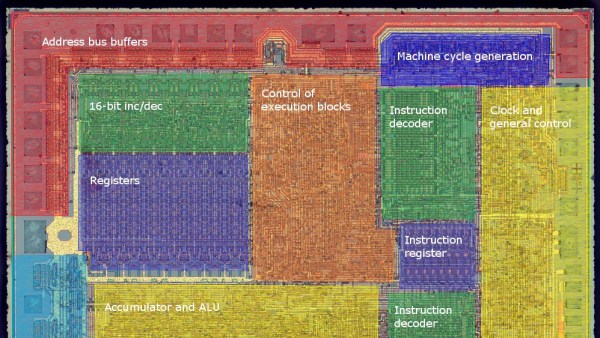
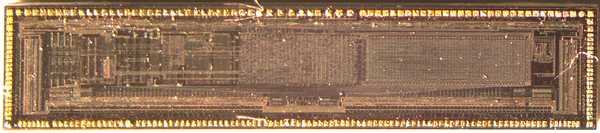
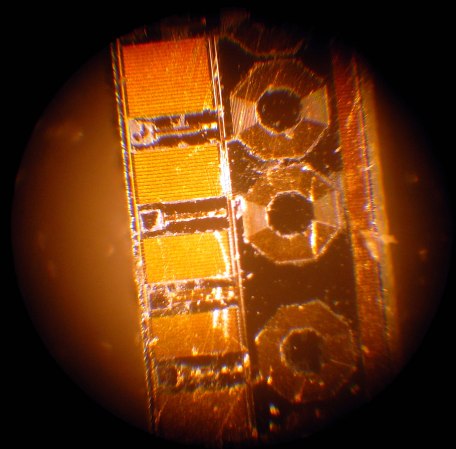
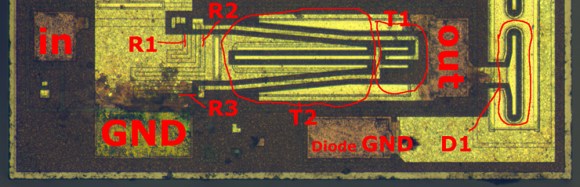
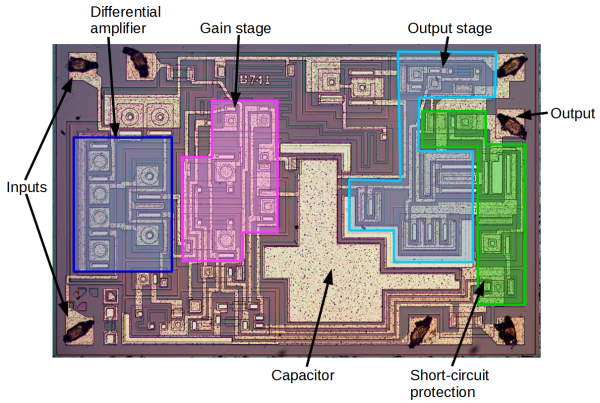
 Rather than risk the boiling acid method commonly used to decap epoxy-potted ICs, [Ken] wisely chose a TO-99 can format to attack with a hacksaw. With the die laid bare for his microscope, he was able to locate all the major components and show how each is implemented in silicon. Particularly fascinating is the difference between the construction of NPN and PNP transistors, and the concept of “current mirrors” as constant current sources. And he even whipped up a handy interactive chip viewer – click on something in the die image and find out which component it is on the 741 schematic. Very nice.
Rather than risk the boiling acid method commonly used to decap epoxy-potted ICs, [Ken] wisely chose a TO-99 can format to attack with a hacksaw. With the die laid bare for his microscope, he was able to locate all the major components and show how each is implemented in silicon. Particularly fascinating is the difference between the construction of NPN and PNP transistors, and the concept of “current mirrors” as constant current sources. And he even whipped up a handy interactive chip viewer – click on something in the die image and find out which component it is on the 741 schematic. Very nice.
We’ve seen lots of chip decappings before, including this reveal of TTL and CMOS logic chips. It’s nice to see the guts of the venerable 741 on display, though, and [Ken]’s tour is both a great primer for the newbie and a solid review for the older hands. Don’t miss the little slice of history he included at the end of the post.

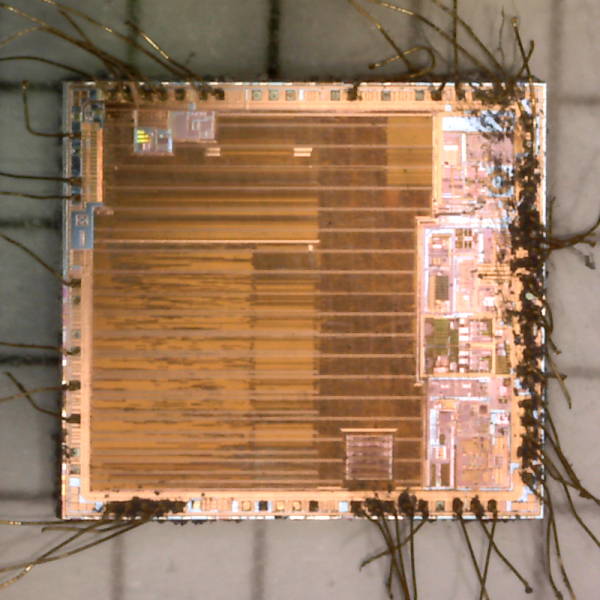
 [Jelmer] was curious to know if the price difference was all in the software. And in order to verify this decided that decapping was the only thing to do!
[Jelmer] was curious to know if the price difference was all in the software. And in order to verify this decided that decapping was the only thing to do!