Oh, iPhone Dev Team, you are a hoot. It isn’t that you managed to jailbreak the iPhone 2.0 firmware on the day of its release, although we can’t help but smirk at that. It isn’t even that you revealed your handiwork in a playful way. We simply love that you expertly work us into a frenzy for the new jailbreak installer with few casual images and some aloof words. Now give us the installer before we get too antsy, please.
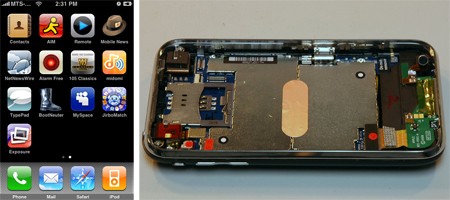
Not to be outshined, though, iFixit has posted a full iPhone 3G teardown, stripping away the sleek casing to feast on the goodness inside. They found some interesting changes from the last model: the glass screen, for example, is no longer glued to the LCD, which will no doubt make repairs less expensive. The battery is also unsoldered, meaning you won’t have to send the phone in for repair if the only battery needs maintenance.