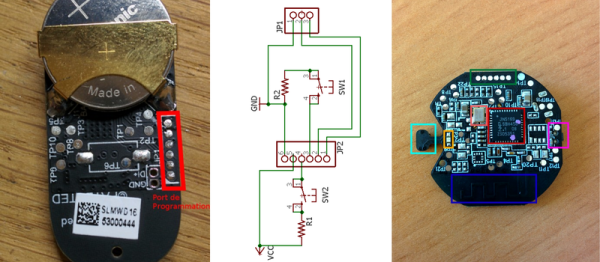
French hacker [akila] is building up a home automation system. In particular, he’s been working with the “SmartHome” series of gadgets made by Chinese smartphone giant, Xiaomi. First, he started off by reverse-engineering their very nicely made temperature and humidity sensor. (Original in French, hit the translate button in the lower right.) With that under his belt, he opened up the PIR motion sensor unit to discover that it has the same debugging pinouts and the same processor. Almost too easy.
For a challenge, [akila] decided it was time to implement something useful in one of these gadgets: a ZigBee sniffer so that he can tell what’s going on in the rest of his home network. He built a USB/serial programming cable to work with the NXP JN5169’s bootloader, downloaded the SDK, and rolled up his sleeves to get to work.
While trolling through the SDK, he found some interesting firmware called “JennicSniffer”. Well, that was easy. There’s a demo version of a protocol analyzer that he used. It would be cool to get this working with Wireshark, but that’s a project for another day. [Akila] got far enough with the demo analyzer to discover that the packets sent by the various devices in the home network are encrypted. That’s good news for the security-conscious out there and stands as the next open item on [akila]’s to-do list.
We don’t see as many ZigBee hacks as we’d expect, but they’ve definitely got a solid niche in home automation because of commercial offerings like Philips Hue and Wink. And of course, there’s the XBee line of wireless communications modules. We just wrote up a ZigBee hack that aims to work with the Hue system, though, so maybe times are changing?