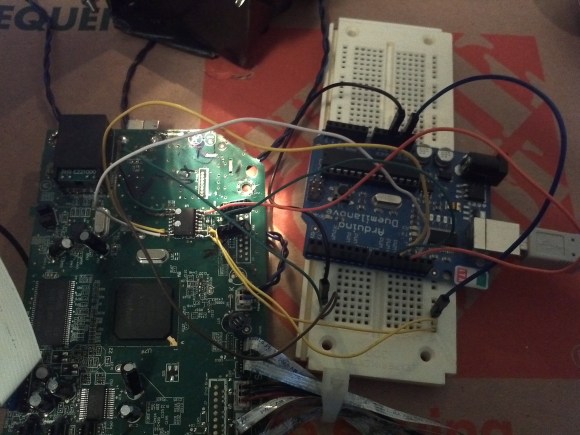
[Juan Carlos Jiménez] has reverse engineered a router — specifically, a Huawei HG533. While that in itself may not sound substantial, what he has done is write a series of blog posts which can act as a great tutorial for anyone wanting to get started with sniffing hardware. Over the five part series, he walks through the details of identifying the hardware serial ports which open up the doors to the firmware and looking at what’s going on under the hood.
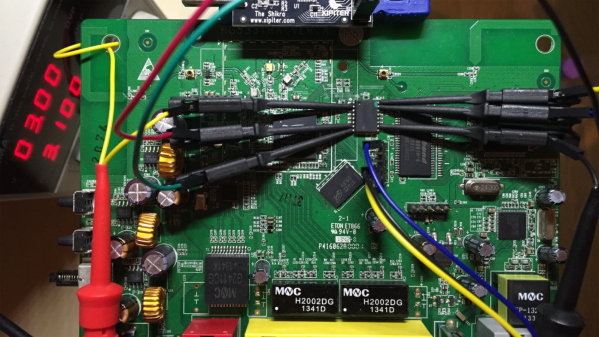
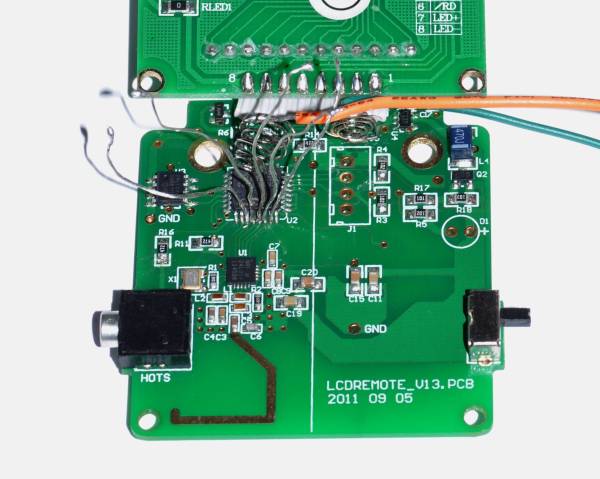
The first part deals with finding the one or several debug ports on the hardware and identifying the three important pins – Rx, Tx and GND. That’s when he shows novices his first trick – shining a flashlight from under the PCB to find the pins that have trace connections (most likely Rx and Tx), those that don’t have any connections (most likely CTS and DTR) and those that have connections to the copper pour planes (most likely VCC and GND). The Tx signal will be pulled up and transmitting data when the device is powered up, while the Rx signal will be floating, making it easy to identify them. Finding the Baud rate, though, will require either a logic analyser, or you’ll have to play a bit of a guessing game.
Once you have access to the serial port and know its baud rate, it’s time to hook it up to your computer and use any one of the several ways of looking at what’s coming out of there — minicom, PuTTY or TeraTerm, for example. With access to the devices CLI, and some luck with finding credentials to log in if required, things start getting interesting.
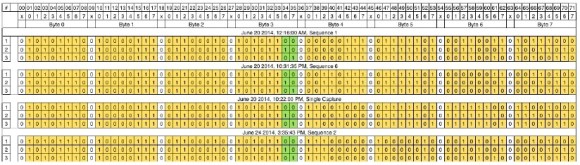
Over the next part, he discusses how to follow the data paths, in this case, looking at the SPI signals between the main processor and the flash memory, and explaining how to use the logic analyser effectively and decode the information it captures. Moving further, he shows how you can hook up a USB to SPI bridge, connect it to the flash memory, take a memory dump of the firmware and read the extracted data. He wraps it up by digging in to the firmware and trying to glean some useful information.
It’s a great series and the detailed analysis he does of this particular piece of hardware, along with providing a lot of general tips, makes it a perfect starting point for those who need some help when getting started on debugging hardware.
Thanks, [gnif] for posting this tip.