The world is full of single board computers that want a slice of the Raspberry Pi action. Most of them are terrible. But fools and their money, yadda yadda, and there’s a new sucker born every minute. The latest contender to the Raspberry Pi is the Atomic Pi. It’s an x86-based single board computer that costs $35, shipped to your door. Is it worth it? Is it even in the same market as a Raspberry Pi? Or is it just a small budget computer without a box? I have no idea.
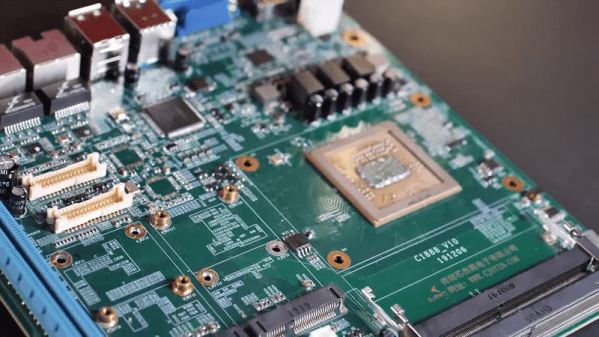
With that said, the Atomic Pi comes with an Intel Atom x5-Z8350 with Intel HD Graphics (Cherry Trail). There is 2 GB of DDR3L-16000, 16 GB of eMMC, and an SD slot for storage. Connectivity is a full HDMI port (primary audio out), USB 3.0 and 2.0 ports, a Mediatec RT5572 used for WiFi, a Qualcomm CSR8510 for Bluetooth 4.0, a “Legitimate licensed BIOS”, and a real-time clock. Overall, you’re looking at a top-of-the-line tablet computer from four years ago. One that would run Windows.
To use all the features of the Atomic Pi, you will need to buy a $15 breakout board to supply power to the board, and use a large industrial power supply, the kind you would normally find bolted to a RepRap or a homemade CNC machine. You will need to supply both 5 V and 12 V to the board if you would like to use the Class D audio amplifier, but if you only want to use audio over HDMI, supplying only 5 V will do. If you want to boot this board, it looks like you’ll need to bring a USB/TTL cable to make everything work. This may be a tough sell to a crowd with zero experience booting a bare Linux system. That said, it runs Nintendo 64 emulators well, which is the only reason people buy Raspberry Pis anyway.
Is the Atomic Pi the single board computer you need? I don’t know. But we’ve got an Atomic Pi on order, and we’re ready to go with a full review when it show up.