While typing away on our DIN, PS/2, USB or Bluetooth keyboards one of the questions which we rarely concern ourselves with is that of how the keyboard registers which keys we’re pressing. One exception here is when the keyboard can only register a limited number of simultaneous keypresses (rollover). Even though most keyboards today use a matrix which connects the keys, there are many configuration choices even here, which much like other keyboard configurations come with their own advantages and disadvantages. As a good primer we can look at this article by [Daniel Beardsmore] as he takes us through both historical and current-day keyboards.
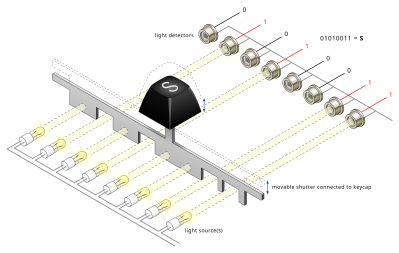
Especially before it was realistic to just put an entire microcontroller with a look-up table into every keyboard, more inventive approaches were required to not only register keypresses, but also encode them for the host computer. The photoelectric approach of the 1960s was one such encoding method, before diode matrices became popular, along with more exotic encoding switches that contained their code already hard-wired on their multitude of pins. One inevitable limitation with these was that of a lack of multi-key support, leading to the development of matrix scan technology around 1970.
Matrix scanning keyboards allow for multiple key presses at the same time, tackle debouncing of keys and were at the forefront of what gives us the ubiquitous and generally boringly reliable keyboards which we use today.