Car keys these days are remarkably complex beasts. Covered in buttons and loaded with security transponders, they often cost hundreds of dollars to replace if you’re unlucky enough to lose them. However, back in the day, keys used to just be keys — a hunk of metal in a mechanical pattern to move some levers and open a door. Thus, you could reshape a wrench into a key for an old car if that was something you really wanted to do.
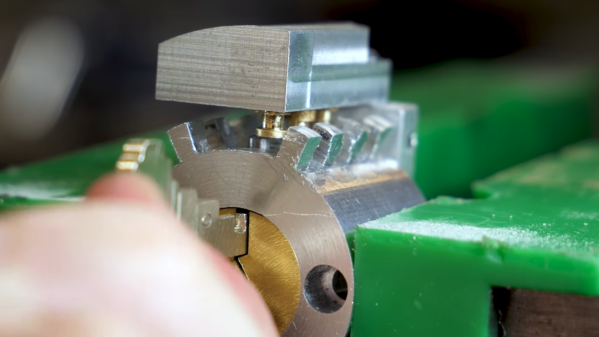
The concept is simple. Take a 12mm ratcheting wrench, and shape the flat section into a profile matching that of a key for an older car without any electronic security features. The first step is to cut down the shaft, before grinding it down to match the thickness and width of the original key.
The profile of the key is then drawn onto the surface, and a Dremel used with a cutting disc to create the requisite shape. Finally, calipers are used to mark out the channels to allow the key to slide into the keyway, before these are also machined with the rotary tool.
Filing and polishing cleans up the final result to create a shiny, attractive ratchet wrench key. Even better, it does a great job of opening the car, too.
Similar machining techniques can be used to duplicate a key from just a photo (something I did back in 2019 to prank my friend). Alternatively, 3D printing can be great for reproducing even high-security keys. Video after the break.
Continue reading “Making A Car Key From A Ratcheting Wrench”