Single-board computers have been around a long time: today you might be using a Raspberry Pi, an Arduino, or an ESP32, but three decades ago you might find yourself programming a KIM-1, an Intel SDK-85, or a Motorola 68000 Educational Computer Board. These kind of boards were usually made by processor manufacturers to show off their latest chips and to train engineers who might use these chips in their designs.
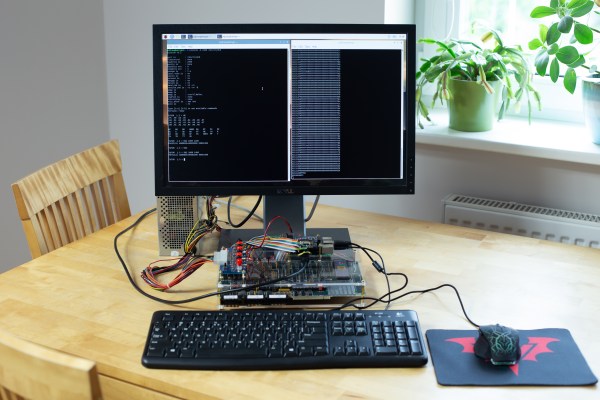
[Adam Podstawczyński] found himself trying to operate one of these Motorola ECBs from 1981. This board contains a 68000 CPU (as used in several Macintoshes and Amigas), 32 kB of RAM, and a ROM program called TUTOR. Lacking any keyboard or monitor connections, the only way to communicate with this system is a pair of serial ports. [Adam] decided to make the board more accessible by adding a Raspberry Pi extended with an RS232 Hat. This add-on board comes with two serial ports supporting the +/- 12 V signal levels used in older equipment.
It took several hours of experimenting, debugging, and reading the extensive ECB documentation to set up a reliable connection; as it turns out, the serial ports can operate in different modes depending on the state of the handshake lines. When the Pi’s serial ports were finally set up in the right mode, the old computer started to respond to commands entered in the terminal window. The audio interface, meant for recording programs on tape, proved more difficult to operate reliably, possibly due to deteriorating capacitors. This was not a great issue, because the ECB’s second serial port could also be used to save and load programs directly into its memory.
With the serial connections working, [Adam] then turned to the aesthetics of his setup and decided to make a simple case out of laser-cut acrylic and metal spacers. Custom ribbon cables for the serial ports and an ATX break-out board for power connections completed the project, and the 40-year-old educational computer is now ready to educate its new owner on all the finer points of 68000 programming. In the video (embedded after the break) he shows the whole process of getting the ECB up and running.
[Adam] made a similarly clever setup with a Commodore 64 and an Arduino earlier. [Jeff Tranter] recreated a similar 68000 development board from scratch. And a few years ago we even featured our own custom-built 68k computer.
Continue reading “Motorola 68000 SBC Runs Again With A Raspberry Pi On Top”