According to [Venn Stone], technical producer over at LinuxGameCast, the Sony a5000 is still a solid option for those looking to shoot 1080p video despite being released back in 2014. But while the camera is lightweight and affordable, it does have some annoying quirks — namely an overlay on the HDMI output (as seen in the image above) that can’t be turned off using the camera’s normal configuration menu. But as it so happens, using some open source tools and the venerable telnet, you can actually log into the camera’s operating system and fiddle with its settings directly.
As explained in the write-up, the first step is to install Sony-PMCA-RE, a cross-platform suite of tools developed for reverse engineering and modifying Sony cameras. With the camera connected via USB, this will allow you to install a program on the camera called Open Memories Tweak. This unlocks some developer options on the camera, such as spawning a telnet server on its WiFi interface.
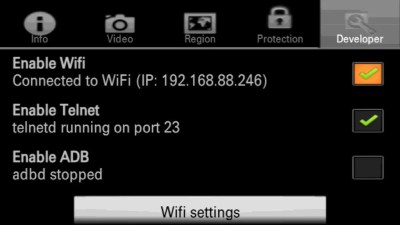 With the a5000 connected to your wireless network, you point your telnet client to its IP address and will be greeted by a BusyBox interface that should be familiar to anyone who’s played with embedded Linux gadgets. The final step is to invoke the proper command,
With the a5000 connected to your wireless network, you point your telnet client to its IP address and will be greeted by a BusyBox interface that should be familiar to anyone who’s played with embedded Linux gadgets. The final step is to invoke the proper command, bk.elf w 0x01070a47 00, which sets the specific address of the camera’s configuration file to zero. This permanently disables the HDMI overlay, though it can be reversed by running the command again and setting the byte back to 01.
As you might expect, the Sony-PMCA-RE package is capable of quite a bit more than just unlocking a telnet server. While it might not be as powerful as a firmware modification such as Magic Lantern for Canon’s hardware, those looking for a hackable camera that won’t break the bank might want to check out the project’s documentation to see what else is possible.
Continue reading “Telnet Gets Stubborn Sony Camera Under Control”


















