Anyone who’s ever spent time in a woodworking shop knows how much dust is produced when cutting, sanding, and so on. [Tim] of Pilson Guitars was looking to outfit his shop with centrifugal dust separators to combat the problem, which are supposed to remove over 99% of the sawdust particles right out of the air. Unfortunately, they can cost thousands of dollars. So he decided to try making his own.
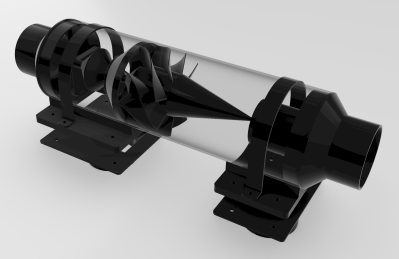
Using a clear PVC tube and 100 hours of printing on his Prusa i3 MK3, his CAD file had come to life, ready to use the power of centrifugal air to leave just enough fine dust in the output port to have a HEPA filter handle the remainder. Unfortunately, initial testing showed that a single dust separator filtered out far less than 90%, and even adding a second unit bumped that up to only 94.2%. Still impressive, but this would clog up a HEPA filter in no time. Thus [Tim] had a second try at it, after a range of helpful comments to the first video.
Changes included a different design for the impeller blades to improve the vortex, as well as attempting to run the system in series. Sadly more issues cropped up, with apparently the air also seeking a way via the collection bins that has [Tim] rethinking more aspects of the design. He has made the design files (STEP and more) available on GitHub for perusal by the community and hopefully some constructive input on how to DIY such dust separation system.
Over the years, we’ve seen many different approaches to the problem of dust collection. We’ve covered other 3D printed solutions if your printer is looking for something to do, but if you’d prefer something a little more low-tech, this traffic cone dust separator is particularly clever.
Continue reading “Printed Centrifugal Dust Separator Stays On Budget”