[TheStaticTurtle] built a custom controller for automating his garage doors. He wanted to retain the original physical button and RF remote control interfaces while adding a more modern wireless control accessible from his internet connected devices. Upgrading an old system is often a convoluted process of trial and error, and he had to discard a couple of prototype versions which didn’t pan out as planned. But luckily, the third time was the charm.
The original door-closer logic was pretty straightforward. Press a button and the door moves. If it’s not going in the desired direction, press the button once again to stop the motor, and then press it a third time to reverse direction. With help from the user manual diagrams and a bit of reverse-engineering, he was able to get a handle on how to plan out his add-on controller to interface with the old system.
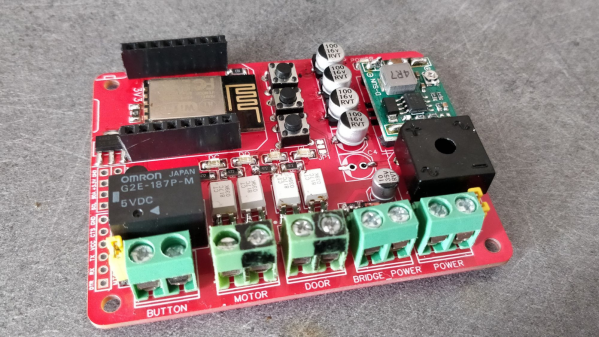
There are many micro-controller options available these days when you want to add IoT to a project, but [TheStaticTurtle] decided to use the old faithful ESP8266 as the brains of his new controller. For his add-on board to work, he needed to detect the direction in which the motor was turning, and detect the limit switches when the door reached end of travel in either direction. Finally, he needed a relay contact in parallel with the activation button to send commands remotely.
To sense if the motor was moving in the “open” or “close” direction, he used a pair of back-to-back opto-couplers in parallel with the motor terminals. He connected another pair of opto-couplers across the two end-limit switches which indicated when the door was fully open or closed, and shut off the motor supply. Finally, a GPIO from the ESP8266 actuates a relay to send the door open and close commands. The boards were designed in EasyEDA and with a quick turnaround from China, he was able to assemble, test and debug his boards pretty quickly.
The code was written using the Arduino IDE and connects the ESP8266 to the MQTT server running on his home automation computer. The end result is a nice dashboard with three icons for open, close and stop, accessible from all the devices connected to his home network. A 3D printed enclosure attaches outside the original control box to keep things tidy. Using hot melt glue as light pipes for the status LED’s is a pretty nifty hack. If you are interested in taking a deeper look at the project, [TheStaticTurtle] has posted all resources on his Github repository.