Time is of the essence in almost every emergency situation, especially when it comes to wildfires. A wind-driven fire can roar across a fuel-rich landscape like a freight train, except one that can turn on a dime or jump a mile-wide gap in a matter of seconds. Usually, the only realistic defense against fires like these is to get the hell out of their way as soon as possible and make room for the professionals to do what they can to stop the flames.
Unfortunately, most people living in areas under threat of wildfires and other natural disasters are often operating in an information vacuum. Official channels take time to distribute evacuation orders, and when seconds count, such delays can cost lives. That’s the hole that Watch Duty seeks to fill.
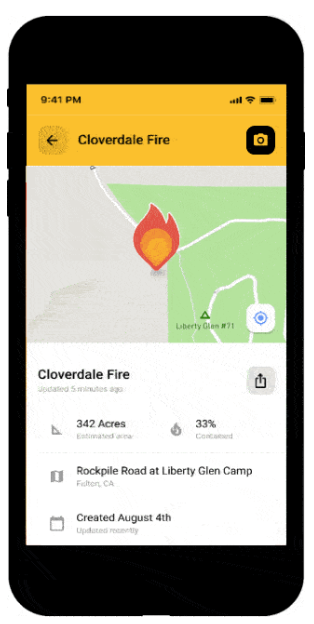 Watch Duty is a non-profit wildfire alerting, mapping, and tracking service that provides near-real-time information to those living in wildfire country. Their intelligence is generated by a network of experienced fire reporters, who live in wildfire-prone areas and monitor public service radio transmissions and other sources to get a picture of what’s going on in their specific area. When the data indicate an incident is occurring, maps are updated and alerts go out via a smartphone app. Reporters have to abide by a strict code of conduct designed to ensure the privacy of citizens and the safety of first responders.
Watch Duty is a non-profit wildfire alerting, mapping, and tracking service that provides near-real-time information to those living in wildfire country. Their intelligence is generated by a network of experienced fire reporters, who live in wildfire-prone areas and monitor public service radio transmissions and other sources to get a picture of what’s going on in their specific area. When the data indicate an incident is occurring, maps are updated and alerts go out via a smartphone app. Reporters have to abide by a strict code of conduct designed to ensure the privacy of citizens and the safety of first responders.
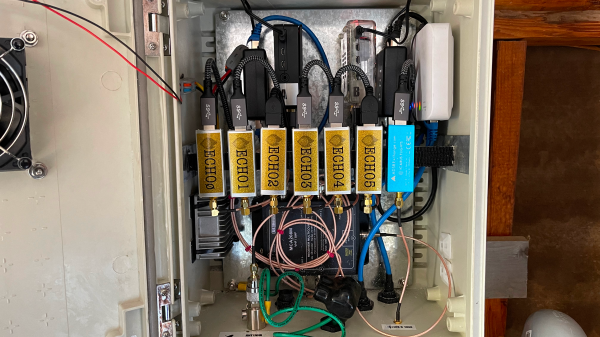
While Watch Duty’s network covers a substantial area of California — the only state covered so far — there were still a significant number of dead zones, mostly in the more remote areas of the Sierra Nevada Mountains and in the northern coastal regions. To fill these gaps, Watch Duty recently launched Watch Duty Echo, which consists of a network of remote listening posts.
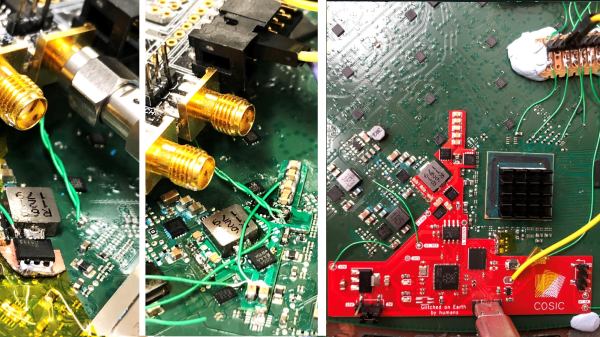
Each station is packed with RTL-SDR receivers that cover a huge swath of spectrum used by the local fire, law enforcement, EMS agencies — any organization likely to be called to respond to an incident. In addition, each station has an SDR dedicated to monitoring ADS-B transponders and air band frequencies, to get a heads-up on incidents requiring aerial support. The listening posts have wideband discone antennas and a dedicated 1090-MHz ADS-B antenna, with either a cellular modem or a Starlink terminal to tie into the Watch Duty network.
Hats off to the folks at Watch Duty for putting considerable effort into a system like this and operating it for the public benefit. Those who choose to live close to nature do so at their own risk, of course, but a citizen-driven network that leverages technology can make that risk just a little more manageable.