When you think of world-changing devices, you usually don’t think of the washing machine. However, making laundry manageable changed not only how we dress but how much time people spent getting their clothes clean. So complaining about how laborious our laundry is today would make someone from the 1800s laugh. Still, we all hate the laundry and [Andrew Dupont], in particular, hates having to check on the machine to see if it is done. So he made Laundry Spy.
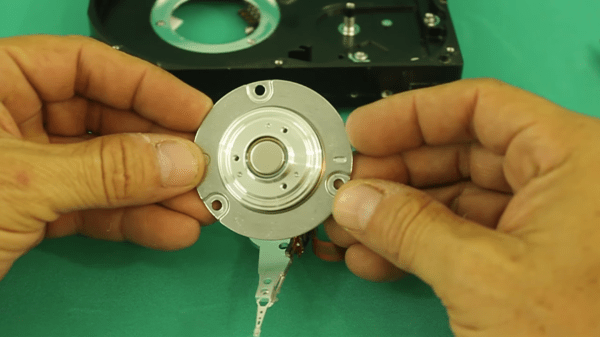
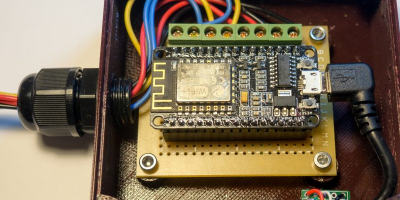 How do you sense when the machine — either a washer or a dryer — is done? [Andrew] thought about sensing current but didn’t want to mess with house current. His machines don’t have LED indicators, so using a light sensor wasn’t going to work either. However, an accelerometer can detect vibrations in the machine and most washers and dryers vibrate plenty while they are running.
How do you sense when the machine — either a washer or a dryer — is done? [Andrew] thought about sensing current but didn’t want to mess with house current. His machines don’t have LED indicators, so using a light sensor wasn’t going to work either. However, an accelerometer can detect vibrations in the machine and most washers and dryers vibrate plenty while they are running.
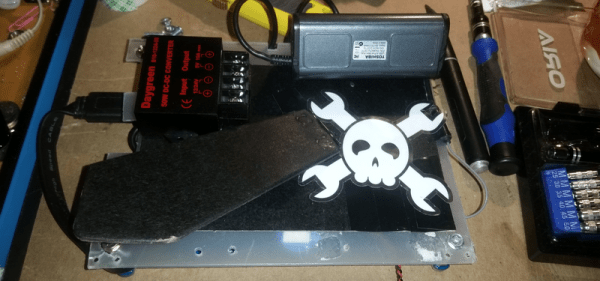
The four-part build log shows how he took an ESP8266 and made it sense when the washer and dryer were done so it could text his cell phone. He’d already done a similar project with an Adafruit HUZZAH. But he wanted to build in some new ideas and currently likes working with NodeMCU. While he was at it he upgraded the motion sensor to an LIS3DH which was cheaper than the original sensor.
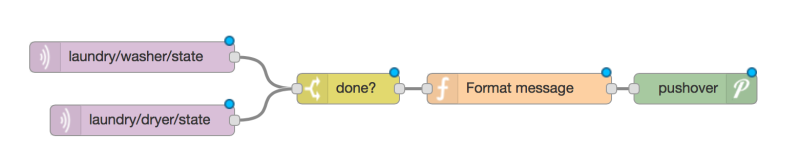
[Andrew] already runs Node – RED on a Raspberry Pi, so incorporating this project with his system was a snap. Of course, you could adapt the approach to lots of other things, as well. The device produces MQTT messages and Node – RED subscribes to them. The Pushover handles the text messaging. Node – RED has a graphical workflow that makes integrating all the pieces very intuitive. Here’s the high-level workflow:
You might wonder why he didn’t just have the ESP8266 talk directly to Pushover. That is possible, of course, but in part 2, [Andrew] enumerates some good reasons for his design. He wants to decouple components in the system for easier future upgrades. And MQTT is simple to publish on the sensor side of things compared to API calls which are handled by the Raspberry Pi for now.
Laundry monitoring isn’t a unique idea and everyone has a slightly different take on it, even some Hackaday authors. If phone notification is too subtle for you, you can always go bigger.