If you’re a reader of Hackaday, then you’ve almost certainly encountered an Espressif part. The twin microcontroller families ESP8266 and ESP32 burst onto the scene and immediately became the budget-friendly microcontroller option for projects of all types. We’ve seen the line expand recently with the ESP32-C3 (packing a hacker-friendly RISC-V core) and ESP32-S3 with oodles of IO and fresh new CPU peripherals. Now we have a first peek at the ESP32-C6; a brand new RISC-V based design with the hottest Wi-Fi standard on the block; Wi-Fi 6.
There’s not much to go on here besides the standard Espressif block diagram and a press release, so we’ll tease out what detail we can. From the diagram it looks like the standard set of interfaces will be on offer; they even go so far as to say “ESP32-C6 is similar to ESP32-C3” so we’ll refer you to [Jenny’s] excellent coverage of that part. In terms of other radios the ESP32-C6 continues Espressif’s trend of supporting Bluetooth 5.0. Of note is that this part includes both the coded and 2 Mbps Bluetooth PHYs, allowing for either dramatically longer range or a doubling of speed. Again, this isn’t the first ESP32 to support these features but we always appreciate when a manufacturer goes above and beyond the minimum spec.
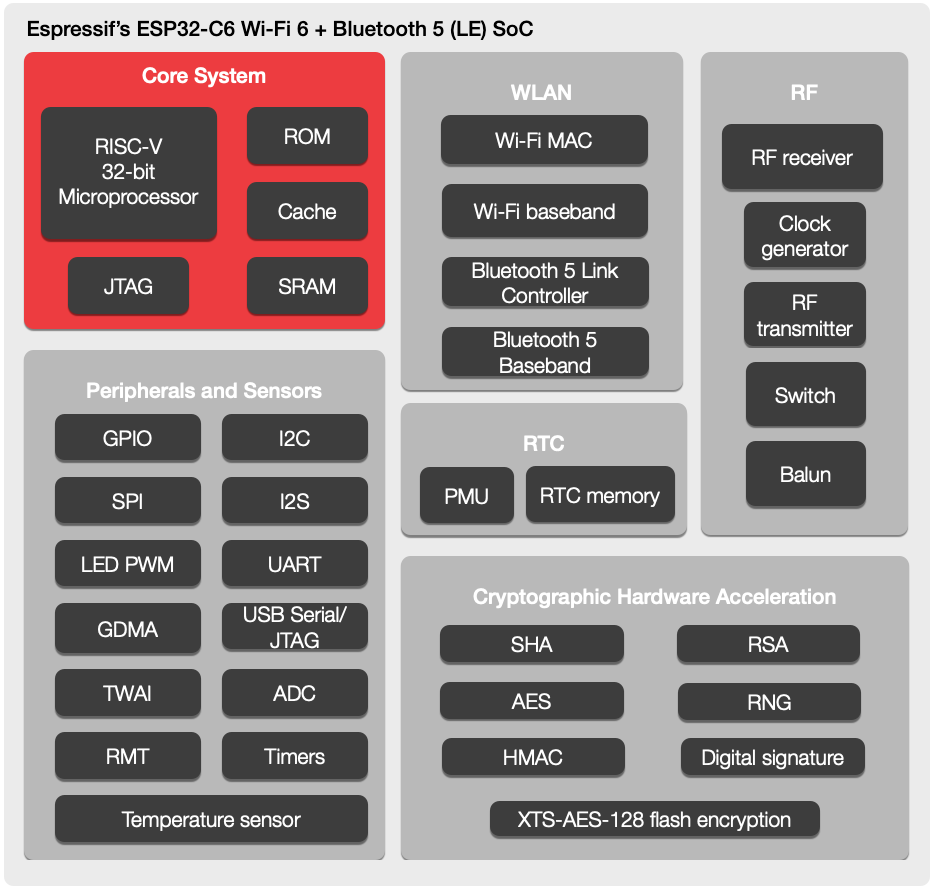
The headline feature is, of course, Wi-Fi 6 (AKA 802.11ax). Unfortunately this is still exclusively a 2.4GHz part, so if you’re looking for 5GHz support (or 6GHz in Wi-Fi 6E) this isn’t the part for you. And while Wi-Fi 6 brings a bevy of features from significantly higher speed to better support for mesh networks, that isn’t the focus here either. Espressif have brought a set of IoT-centric features; two radio improvements with OFDMA and MU-MIMO, and the protocol feature Target Wake Time.
OFDMA and MU-MIMO are both different ways of allowing multiple connected device to communicate with an access point simultaneously. OFDMA allows devices to slice up and share channels more efficiency; allowing the AP more flexibility in allocating its constrained wireless resources. With OFDMA the access point can elect to give an entire channel to a single device, or slice it up to multiplex between more than once device simultaneously. MU-MIMO works similarly, but with entire antennas. Single User MIMO (SU-MIMO) allows an AP and connected device to communicate using a more than one antenna each. In contrast Multi User MIMO (MU-MIMO) allows APs and devices to share antenna arrays between multiple devices simultaneously, grouped directionally.
Finally there’s Target Wake Time, the simplest of the bunch. It works very similarly to the Bluetooth Low Energy (4.X and 5.X) concept of a connection interval, allowing devices to negotiate when they’re next going to communicate. This allows devices more focused on power than throughput to negotiate long intervals between which they can shut down their wireless radios (or more of the processor) to extended battery life.
These wireless features are useful on their own, but there is another potential benefit. Some fancy new wireless modes are only available on a network if every connected device supports them. A Wi-Fi 6 network with 10 Wi-Fi 6 devices and one W-Fi 5 (802.11ac) one may not be able to use all the bells and whistles, degrading the entire network to the lowest common denominator. The recent multiplication of low cost IoT devices has meant a corresponding proliferation of bargain-basement wireless radios (often Espressif parts!). Including new Wi-Fi 6 exclusive features in what’s sure to be an accessible part is a good start to alleviating problems with our already strained home networks.
When will we start seeing the ESP32-C6 in the wild? We’re still waiting to hear but we’ll let you know as soon as we can get our hands on some development hardware to try out.
Thanks to friend of the Hackaday [Fred Temperton] for spotting this while it was fresh!