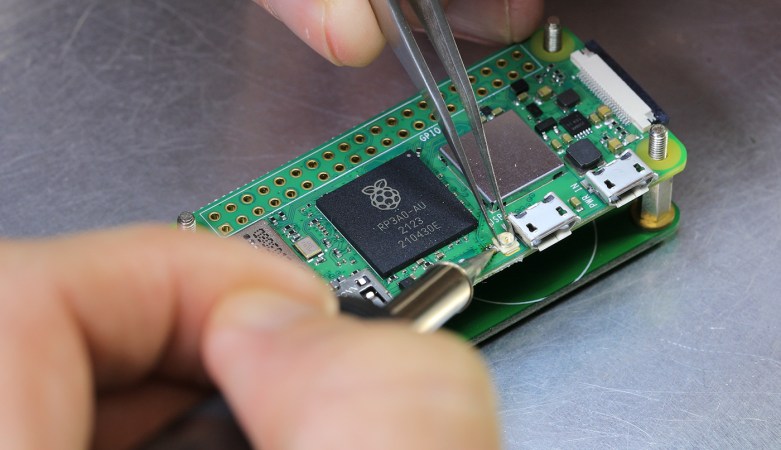
Yagi-Uda antennas, or simply “Yagis”, are directional antennas that focus radio waves to increase gain, meaning that the radio waves can travel further in that direction for a given transmitter power. Anyone might recognize an old TV antenna on a roof that uses this type of antenna, but they can be used to increase the gain of an antenna at any frequency. This one is designed to operate within the frequencies allotted to WiFi and as a result is so small that the entire antenna can be printed directly on a PCB.
The antenna consists of what is effectively a dipole antenna, sandwiched in between a reflector and three directors. The reflector and directors are passive elements in that they interact with the radio wave to focus it in a specific direction, but the only thing actually powered is the dipole in the middle. It looks almost like a short circuit at first but thanks to the high frequencies involved in this band, will still function like any other dipole antenna would. [IMSAI Guy], who created the video linked above which goes over these details also analyzed the performance of this antenna and found it to be fairly impressive as a WiFi antenna, but he did make a few changes to the board for some other minor improvements in performance.
The creator of these antennas, [WA5VJB] aka [Kent Britain] is an antenna builder based in Texas who has developed a few unique styles of antennas produced in non-traditional ways. Besides this small Yagi, there are other microwave antennas available for direction-finding, some wide-band antennas, and log-periodic antennas that look similar to Yagi antennas but are fundamentally different designs. But if you’re looking to simply extend your home’s WiFi range you might not need any of these, as Yagi antennas for home routers can be a lot simpler than you ever imagined.

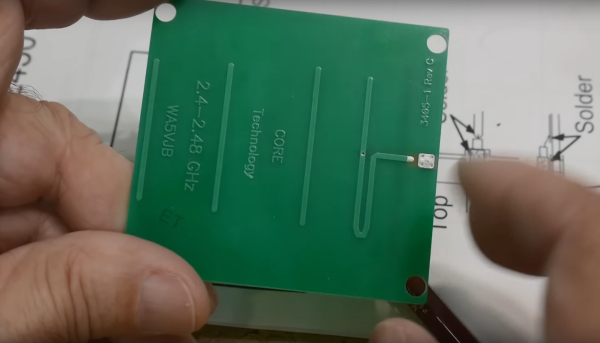
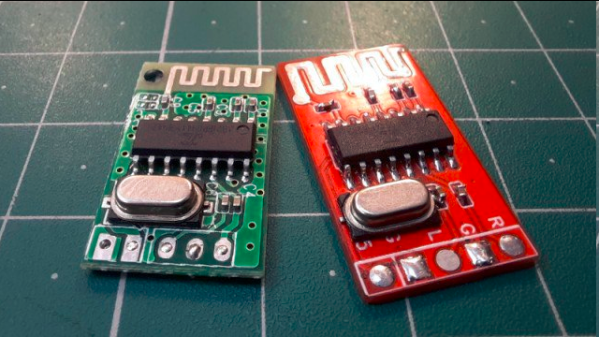
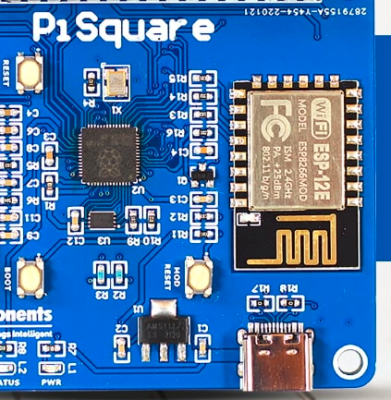
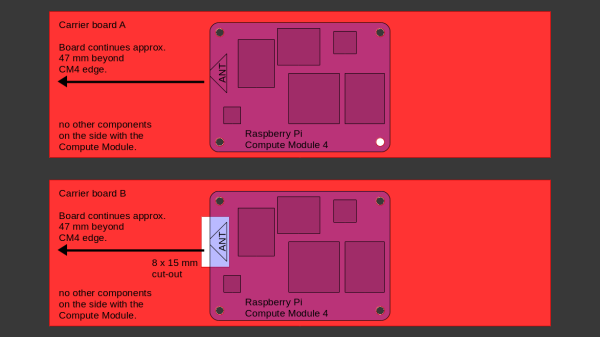
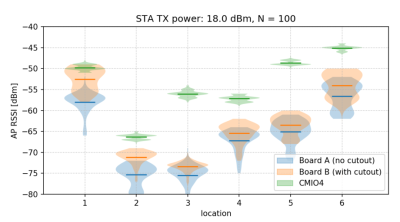 After setting up some test locations and writing a few scripts for ease of testing, [Avian] recorded the experiment data. Having that data plotted, it would seem that, while presence of an under-antenna cutout helps, it doesn’t affect RSSI as much as the module placement does. Of course, there’s way more variables that could affect RSSI results for your own designs – thankfully, the scripts used for logging are available, so you can test your own setups if need be.
After setting up some test locations and writing a few scripts for ease of testing, [Avian] recorded the experiment data. Having that data plotted, it would seem that, while presence of an under-antenna cutout helps, it doesn’t affect RSSI as much as the module placement does. Of course, there’s way more variables that could affect RSSI results for your own designs – thankfully, the scripts used for logging are available, so you can test your own setups if need be.