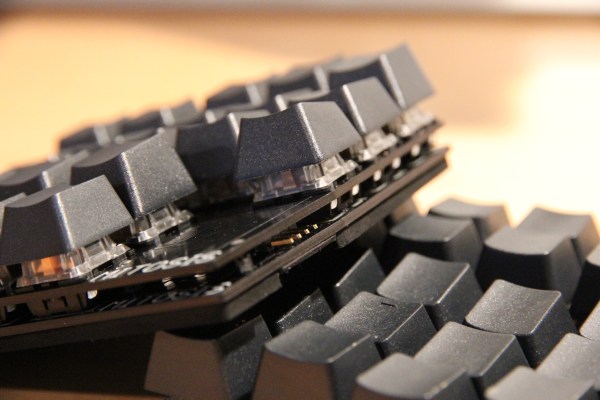
Only a Human would understand the pithy sarcasm in “You had one job”. When [tterev3]’s RopeBot the Robot became sentient and asked “What is my purpose?”, [tterev3] had to lay it out for him quite bluntly – “You cut the rope”. He designed RopeBot (YouTube video embedded below) for one job only – single mission, single use.
A couple of years back, [tterev3] had put up some thick ropes for a low ropes course in his backyard. Over time, the trees grew up, and the ropes became embedded in the tree trunks. Instead of risking his own life and limbs to try cutting them down, he designed RopeBot to do the job for him. It’s built from scavenged electronics and custom 3D printed parts. A geared motor driving a large cogged pulley helped by two smaller, idler wheels helps the bot to scurry up and down the rope. A second geared motor drives a cam reciprocating mechanism, similar to industrial metal cutting saws. A common utility knife is the business end of the bot, helping slice through the rope. A radio receiver and controller is the brains of the bot which drives the two motors through a motor driver board. The remote controller, assembled on a piece of foam, has three switches for Up, Down and Cut. Everything is held together on the 3D printed frame and tied down with a generous use of zip ties, with rubber bands providing spring tension where needed. When the rope has been cut, the RopeBot comes down for a smashing end. It might not look fancy, but it gets the job done. We spy some real ball bearings on the three pulleys meaning [tterev3] didn’t skimp on good design just because it’s a disposable robot. Obviously, he spent a fair amount of time and effort in designing RopeBot.
Once the job is done, most of the electronics and hardware can be recovered and used again while the 3D printed parts could be recycled, making this a really cost-effective way of handling the problem. Like the Disposable Drones we covered earlier, these kind of “use and discard” robots not only make life easier for Humans, but also ensure low economic and ecological impact.


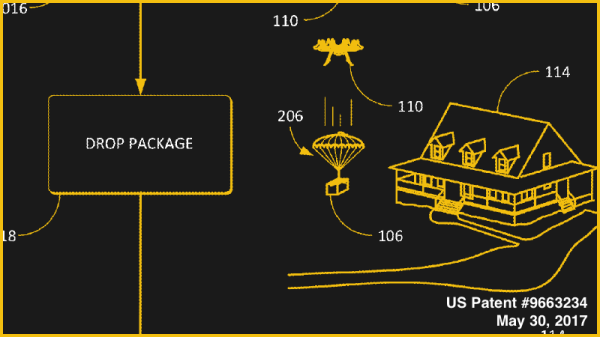
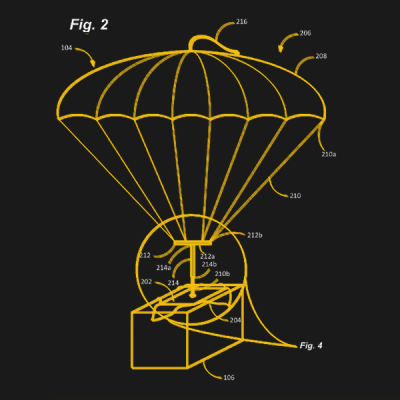 The objective is to paradrop your next delivery and by the looks of the patent images, they plan to use it for everything from eggs to the kitchen sink. Long packages will employ multiple labels with parachutes which will then be monitored using the camera and other sensors on the drone itself to monitor descent.
The objective is to paradrop your next delivery and by the looks of the patent images, they plan to use it for everything from eggs to the kitchen sink. Long packages will employ multiple labels with parachutes which will then be monitored using the camera and other sensors on the drone itself to monitor descent.