PhD students spend their time pursuing whatever general paths their supervisor has given them, and if they are lucky, it yields enough solid data to finally write a thesis without tearing their hair out. Sometimes along the way they result in discoveries with immediate application outside academia, and so it was for [Paul Bupe Jr.], whose work resulted in a rather elegant and simple bend sensor.
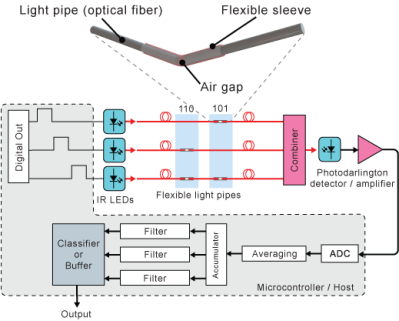 The original research came when shining light along flexible media, including a piece of transparent 3D printer filament. He noticed that when the filament was bent at a point that it was covered by a piece of electrical tape there was a reduction in transmission, and from this he was able to repeat the effect with a piece of pipe over a narrow air gap in the medium.
The original research came when shining light along flexible media, including a piece of transparent 3D printer filament. He noticed that when the filament was bent at a point that it was covered by a piece of electrical tape there was a reduction in transmission, and from this he was able to repeat the effect with a piece of pipe over a narrow air gap in the medium.
Putting these at regular intervals and measuring the transmission for light sent along it, he could then detect a bend. Take three filaments with the air-gap-pipe sensors spaced to form a Gray code, and he could digitally read the location.
He appears to be developing this discovery into a product. We’re not sure which is likely to be more stress, writing up his thesis, or surviving a small start-up, so we wish him luck.