Everyone loves themes. Doesn’t matter if it’s a text editor or a smart display in the kitchen, we want to be able to easily customize its look and feel to our liking. When setting up a new device or piece of software, playing around with the available themes may be one of the first things you do without giving it much thought. After all, it’s not like picking the wrong one is going to do something crazy like silently delete all the files on your computer, right?
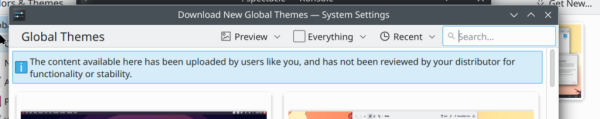
Unfortunately, that’s exactly what happened a few days ago to [JeansenVaars] while trying out a Plasma Global Theme from the KDE Store. According to their Reddit post, shortly after installing the “Gray Layout” theme for the popular Linux graphical environment, the system started behaving oddly and then prompted for a root password. Realizing something didn’t seem right they declined, but at that point, it was already too late for all of the personal files in their home directory.
Continue reading “User Beware: The Fine Line Between Content And Code”