When we first developed telescopes, we started using them on the ground. Humanity was yet to master powered flight, you see, to say nothing of going beyond into space. As technology developed, we realized that putting a telescope up on a satellite might be useful, since it would get rid of all that horrible distortion from that pesky old atmosphere. We also developed radio telescopes, when we realized there were electromagnetic signals beyond visible light that were of great interest to us.
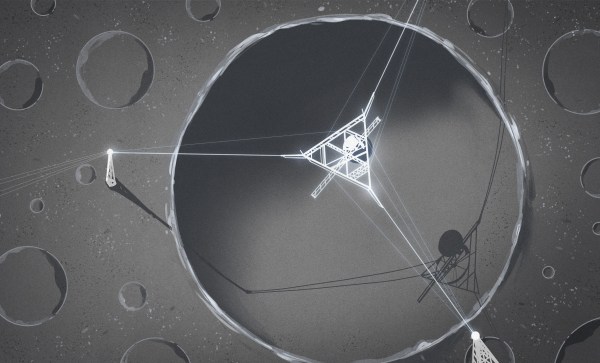
Now, NASA’s dreaming even bigger. What if it could build a big radio telescope up on the Moon?
Continue reading “They Want To Put A Telescope In A Crater On The Moon”