Of all the stories we’d expect to hit our little corner of the world, we never thought that the seedy doings of a now-deceased accused pedophile billionaire would have impacted the intellectual home of the open-source software movement. But it did, and this week Richard Stallman resigned from the Computer Science and Artificial Intelligence Lab at MIT, as well as from the Free Software Foundation, which he founded and served as president. The resignations, which Stallman claims were “due to pressure on MIT and me over a series of misunderstandings and mischaracterizations”, followed the disclosure of a string of emails where he perhaps unwisely discussed what does and does not constitute sexual assault. The emails were written as a response to protests by MIT faculty and students outraged over the university’s long and deep relationship with Jeffrey Epstein, the late alleged pedophile-financier. This may be one of those stories where the less said, the better. If only Stallman had heeded that advice.
They may be the radio stations with the worst programming ever, but then again, the world’s atomic clock broadcasting stations can really keep a beat. One of the oldest of these stations, WWV, is turning 100 this year, and will be adding special messages to its usual fare of beeps and BCD-encoded time signals on a 100-Hz subcarrier. If you tune to WWV at 10 past the hour (or 50 minutes past the hour for WWVH, the time station located in Hawaii) you’ll hear a special announcement. There was also talk of an open house at the National Institute of Standards and Technology complete with a WWV birthday cake, but that has since been limited to 100 attendees who pre-registered.
For the machinists and wannabes out there, the Internet’s machine shop channels all pitched in this week on something called #tipblitz19, where everyone with a lathe or mill posted a short video of their favorite shop tip. There’s a ton of great tip out there now, with the likes of This Old Tony, Abom79, Stefan Gotteswinter, and even our own Quinn Dunki contributing timesaving – and finger saving – tips. Don’t stop there though – there’s a playlist with 77 videos at last count, many of them by smaller channels that should be getting more love. Check them out and then start making chips.
Most of us know that DLP chips, which lie behind the lens of the projectors that lull us to sleep in conference rooms with their white noise and warm exhaust, are a series of tiny mirrors that wiggle around to project images. But have you ever seen them work? Now you can: Huygens Optics has posted a fascinating video deep-dive into the workings of digital light processors. With a stroboscopic camera and a lot of fussy work, the video reveals the microscopic movements of these mirrors and how that syncs up with the rotation of a color filter wheel. It’s really fascinating stuff, and hats off to Huygens for pulling off the setup needed to capture this.
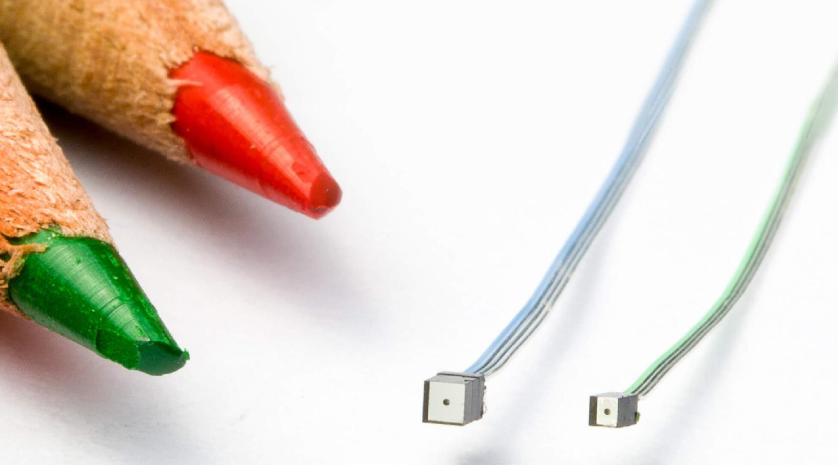 And speaking of tiny optics, get a load of these minuscule digital cameras, aptly described by tipster David Gustafik as “disturbingly small.” We know we shouldn’t be amazed by things like this anymore, but c’mon – they’re ridiculously tiny! According to the datasheet, the smaller one will occupy 1 mm² on a PCB; the larger stereo camera requires 2.2 mm². Dubbed NanEye, the diminutive cameras are aimed at the medical market – think endoscopy – and at wearables manufacturers. These would be a lot of fun to play with – just don’t drop one.
And speaking of tiny optics, get a load of these minuscule digital cameras, aptly described by tipster David Gustafik as “disturbingly small.” We know we shouldn’t be amazed by things like this anymore, but c’mon – they’re ridiculously tiny! According to the datasheet, the smaller one will occupy 1 mm² on a PCB; the larger stereo camera requires 2.2 mm². Dubbed NanEye, the diminutive cameras are aimed at the medical market – think endoscopy – and at wearables manufacturers. These would be a lot of fun to play with – just don’t drop one.
 Our Hack Chats are live community events in the Hackaday.io Hack Chat group messaging. This week we’ll be sitting down on Wednesday, September 25 at 12:00 PM Pacific time. If time zones have got you down, we have a handy time zone converter.
Our Hack Chats are live community events in the Hackaday.io Hack Chat group messaging. This week we’ll be sitting down on Wednesday, September 25 at 12:00 PM Pacific time. If time zones have got you down, we have a handy time zone converter.