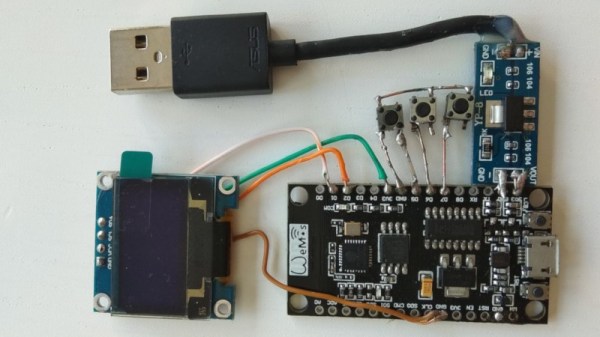
Interfering with radio communications, whether through jamming, deauthing attacks, or other meddling, is generally considered a crime, and one that attracts significant penalties. However, studying such techniques should provide a useful edge in the electronic wars to come. In this vein, [Giorgio Filardi] has recently built a WiFi deauther the size of a credit card.
The device has a simple interface, consisting of 3 buttons and a small OLED screen. It can also be accessed remotely and controlled through a web interface. A NodeMCU ESP8266 board runs the show, using [spacehuhn]’s deauther firmware. The point-to-point construction probably won’t hold up to much rough and tumble out in the field, but it’s fine for a bench test. We’d recommend constructing an enclosure if it was to be used more regularly.
There’s plenty of functionality baked in – the device can scan for networks, perform deauth attacks, and even create spoof networks. It’s a tricky little device that serves to highlight several flaws in WiFi security that are yet to be fixed by the powers that be.
Using one of these devices for nefarious purposes will likely get you into trouble. Experimenting on your own networks can be educational, however, and goes to show that wireless networks are never quite as safe as we want them to be.
If you’re wondering as to the difference between deauthentication and jamming, here’s your primer.