OK, sit down, everyone — we don’t want you falling over and hurting yourself when you learn the news that actually yes, your phone has been listening to your conversations all along. Shocking, we know, but that certainly seems to be what an outfit called Cox Media Group (CMG) does with its “Active Listening” software, according to a leaked slide deck that was used to pitch potential investors. The gist is that the software uses a smartphone’s microphone to listen to conversations and pick out keywords that it feeds to its partners, namely Google, Facebook, and Amazon so that they can target you with directed advertisements. Ever have an IRL conversation about something totally random only to start seeing references to that subject pop up where they never did before? We sure have, and while “relationship mining” seemed like a more parsimonious explanation back in 2017, the state of tech makes eavesdropping far more plausible today. Then there’s the whole thing of basically being caught red-handed. The Big Three all huffed and puffed about how they were shocked, SHOCKED to learn that this was going on, with reactions ranging from outright denial of ever partnering with CMG to quietly severing their relationship with the company. So much for years of gaslighting on this.
eavesdropping12 Articles
Noisy Keyboards Sink Ships
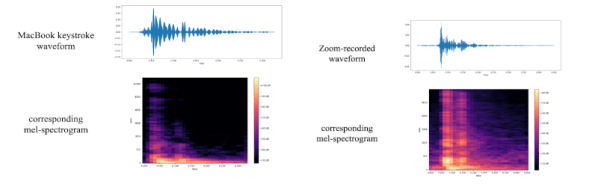
Many of us like a keyboard with a positive click noise when we type. You might want to rethink that, though, in light of a new paper from the UK that shows how researchers trained an AI to decode keystrokes from noise on conference calls.
The researchers point out that people don’t expect sound-based exploits. The paper reads, “For example, when typing a password, people will regularly hide their screen but will do little to obfuscate their keyboard’s sound.”
The technique uses the same kind of attention network that makes models like ChatGPT so powerful. It seems to work well, as the paper claims a 97% peak accuracy over both a telephone or Zoom. In addition, where the model was wrong, it tended to be close, identifying an adjacent keystroke instead of the correct one. This would be easy to correct for in software, or even in your brain as infrequent as it is. If you see the sentence “Paris im the s[ring,” you can probably figure out what was really typed.
We’ve seen this done before, but this technique raises the bar. As sophisticated as keyboard listening was back in the 1970s, you can only imagine what the three-letter agencies can do these days.
In the meantime, the mitigation for this particular threat seems obvious — just start screaming whenever you type in your password.
Audio Eavesdropping Exploit Might Make That Clicky Keyboard Less Cool
Despite their claims of innocence, we all know that the big tech firms are listening to us. How else to explain the sudden appearance of ads related to something we’ve only ever spoken about, seemingly in private but always in range of a phone or smart speaker? And don’t give us any of that fancy “confirmation bias” talk — we all know what’s really going on.
And now, to make matters worse, it turns out that just listening to your keyboard clicks could be enough to decode what’s being typed. To be clear, [Georgi Gerganov]’s “KeyTap3” exploit does not use any of the usual RF-based methods we’ve seen for exfiltrating data from keyboards on air-gapped machines. Rather, it uses just a standard microphone to capture audio while typing, building a cluster map of the clicks with similar sounds. By analyzing the clusters against the statistical likelihood of certain sequences of characters appearing together — the algorithm currently assumes standard English, and works best on clicky mechanical keyboards — a reasonable approximation of the original keypresses can be reconstructed.
If you’d like to see it in action, check out the video below, which shows the algorithm doing a pretty good job decoding text typed on an unplugged keyboard. Or, try it yourself — the link above implements KeyTap3 in-browser. We gave it a shot, but as a member of the non-mechanical keyboard underclass, it couldn’t make sense of the mushy sounds it heard. Then again, our keyboard inferiority affords us some level of protection from the exploit, so there’s that.
Editors Note: Just tried it on a mechanical keyboard with Cherry MX Blue switches and it couldn’t make heads or tails of what was typed, so your mileage may vary. Let us know if it worked for you in the comments.
What strikes us about this is that it would be super simple to deploy an exploit like this. Most side-channel attacks require such a contrived scenario for installing the exploit that just breaking in and stealing the computer would be easier. All KeyTap needs is a covert audio recording, and the deed is done.
Continue reading “Audio Eavesdropping Exploit Might Make That Clicky Keyboard Less Cool”
Eavesdropping By LED
If you ever get the feeling someone is watching you, maybe they are listening, too. At least they might be listening to what’s coming over your computer speakers thanks to a new attack called “glow worm.” In this novel attack, careful observations of a power LED on a speaker allowed an attacker to reproduce the sound playing thanks to virtually imperceptible fluctuations in the LED brightness, most likely due to the speaker’s power line sagging and recovering.
You might think that if you could see the LED, you could just hear the output of the speaker, but a telescope through a window 100 feet away appears to be sufficient. You can imagine that from a distance across a noisy office you might be able to pull the same trick. We don’t know — but we suspect — even if headphones were plugged into the speakers, the LED would still modulate the audio. Any device supplying power to the speakers is a potential source of a leak.
The Last Days Of The Wild West
We loved it a few weeks ago when an international team of hackers managed to record and decode telemetry and images from SpaceX launches. And now it looks like SpaceX has started encrypting it all in response. Booo!
Decoding satellite and other space ship transmissions has been a great hacker pastime. Most recently, we’ve seen a group working on listening in to the Chinese Tianwen-1 Mars probe shortly after its launch, but listening to the Deep Space Network or even just decoding weather satellite broadcasts can give folks a reason to stretch their radio muscles.
We understand that SpaceX runs some contract missions for US gov’t agencies that don’t appreciate leaking info about their satellite’s whereabouts, but for non-secret missions, we don’t see the harm in letting the amateurs listen in over their shoulder. Maybe they’re doing it for PR reasons if/when something goes badly wrong?
 Whatever the reasons, it’s a shame. Space has been open to hackers for a long time, knowingly in the case of amateur satellites, and unknowingly in the case of many other satellites which until the mid-90s had command channels that were unencrypted. (I’ll have to stick with “unnamed sources” on this one, but I do know a person who has rotated a satellite that he or she didn’t own.) There’s a lot to be learned by listening to signals from above, and while you can still decode weather satellite data yourself, it’s not quite as sexy as downloading images straight from a Falcon 9.
Whatever the reasons, it’s a shame. Space has been open to hackers for a long time, knowingly in the case of amateur satellites, and unknowingly in the case of many other satellites which until the mid-90s had command channels that were unencrypted. (I’ll have to stick with “unnamed sources” on this one, but I do know a person who has rotated a satellite that he or she didn’t own.) There’s a lot to be learned by listening to signals from above, and while you can still decode weather satellite data yourself, it’s not quite as sexy as downloading images straight from a Falcon 9.
The cool hand for SpaceX to have played would have been to say “of course — we broadcast unencrypted as PR to our biggest fans” but it looks instead like they simply didn’t think that anyone would be listening in, and this caught them by surprise and they panicked. In 2021, with something as complicated as a space mission, that’s a little bit embarrassing. Anyway, to those of you who managed to get in before encryption, kudos!
Listening To An IPhone With AM Radio
Electronic devices can be surprisingly leaky, often spraying out information for anyone close by to receive. [Docter Cube] has found another such leak, this time with the speakers in iPhones. While repairing an old AM radio and listening to a podcast on his iPhone, he discovered that the radio was receiving audio the from his iPhone when tuned to 950-970kHz.
[Docter Cube] states that he was able to receive the audio signal up to 20 feet away. A number of people responded to the tweet with video and test results from different phones. It appears that iPhones 7 to 10 are affected, and there is at least one report for a Motorola Android phone. The amplifier circuit of the speaker appears to be the most likely culprit, with some reports saying that the volume setting had a big impact. With the short range the security risk should be minor, although we would be interested to see the results of testing with higher gain antennas. It is also likely that the emission levels still fall within FCC Part 15 limits.
Microphones Listen To Your… Monitor?
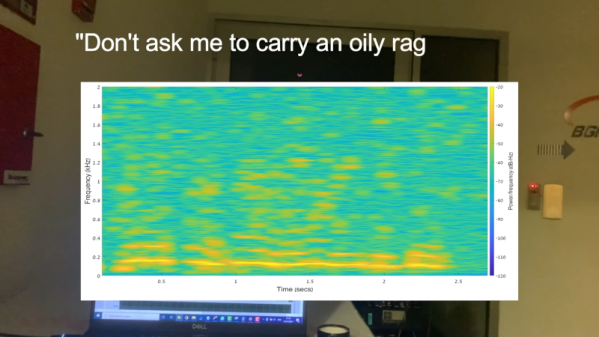
A song by Rockwell, “Somebody’s Watching Me” might be the anthem for the tin foil hat crowd. But a new paper reveals that it might be just as scary to have someone listening to you. Researchers have used common microphones to listen in on computer monitors. The demonstration includes analyzing audio to determine input from virtual keyboards and even a way to tell if people are surfing the web during a Google Hangout session.
Reading monitors based on electronic emissions is nothing new — ask Wim van Eck or read about TEMPEST. What makes this worrisome is that we constantly have live microphones around our computers. Webcams, phones, the latest smart assistant. Even some screens have built-in microphones. According to the paper, you could even pick up data from recorded audio. The paper has three main goals: extract display text, distinguish between different websites on screen, and extracting text entered with a virtual keyboard.
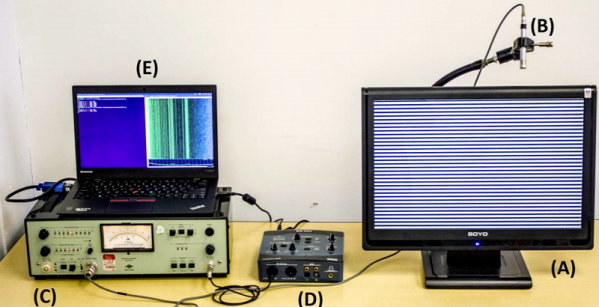
The analysis looked at 31 different screens. There were 12 distinct models from 6 different vendors. They did use a special VGA cable to tap the vertical sync to help manage the data, but they claim this was only an aid and not essential. They also used a high-end sound setup with a 192 kHz sampling rate.
Measuring the sound made by different display patterns was empirical. The authors think the mechanism is from subtle changes in the vibrations of the power supply components due to changes in current consumption. The refresh rate of the monitor also plays a part.
Armed with the proof of concept, the team went on to use an LG V20 cellphone and via a Hangouts call. Imagine if the person on the other end of your call could tell when you were reading Hackaday instead of paying attention to the call.
Different types of monitors need to be learned for best accuracy. It appears that reading small text may have problems, too. Even website detection depends on training. Still, maybe the tin hat people aren’t exactly wrong.
If you want to try your hand at reading the RF emissions, software defined radio is your friend. We’ll be interested to see if anyone duplicates the acoustic method in this paper, though.