Now that November of 2019 has passed, it’s a shame that some of the predictions made in Blade Runner for this future haven’t yet come true. Oh sure, 109 million people living in Los Angeles would be fun and all, but until we get our flying cars, we’ll just have to console ourselves with the ability to “Enhance!” photographs. While the new service, AI Image Enlarger, can’t tease out three-dimensional information, the app is intended to sharpen enlargements of low-resolution images, improving the focus and bringing up details in the darker parts of the image. The marketing material claims that the app uses machine learning, and is looking for volunteers to upload high-resolution images to improve its training set.
We’ve been on a bit of a nano-satellite bender around here lately, with last week’s Hack Chat discussing simulators for CubeSats, and next week’s focusing on open-source thrusters for PocketQube satellites. So we appreciated the timing of a video announcing the launch of the first public LoRa relay satellite. The PocketCube-format satellite, dubbed FossaSat-1, went for a ride to space along with six other small payloads on a Rocket Lab Electron rocket launched from New Zealand. Andreas Spiess has a short video preview of the FossaSat-1 mission, which was designed to test the capabilities of a space-based IoT link that almost anyone can access with cheap and readily available parts; a ground station should only cost a couple of bucks, but you will need an amateur radio license to uplink.
We know GitHub has become the de facto standard for source control and has morphed into a collaboration and project management platform used by everybody who’s anybody in the hacking community. But have you ever wished for a collaboration platform that was a little more in tune with the needs of hardware designers? Then InventHub might be of interest to you. Currently in a limited beta – we tried to sign up for the early access program but seem to have been put on a waiting list – it seems like this will be a platform that brings versioning directly to the ECAD package of your choice. Through plugins to KiCad, Eagle, and all the major ECAD players you’ll be able to collaborate with other designers and see their changes marked up on the schematic — sort of a visual diff. It seems interesting, and we’ll be keeping an eye on developments.
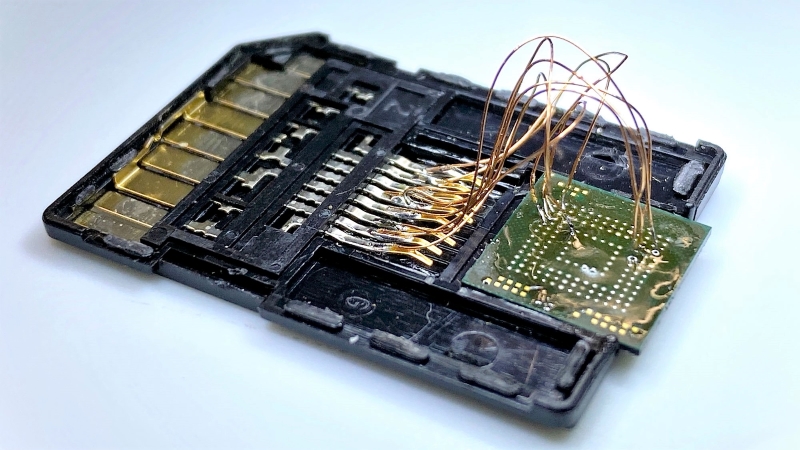 Amazon is now offering a stripped-down version of their Echo smart speaker called Input, which teams up with speakers that you already own to satisfy all your privacy invasion needs on the super cheap — only $10. At that price, it’s hard to resist buying one just to pop it open, which is what Brian Dorey did with his. The teardown is pretty standard, and the innards are pretty much what you’d expect from a modern piece of surveillance apparatus, but the neat trick here involved the flash memory chip on the main board. Brian accidentally overheated it while trying to free up the metal shield over it, and the BGA chip came loose. So naturally, he looked up the pinout and soldered it to a micro-SD card adapter with fine magnet wire. He was able to slip it into a USB SD card reader and see the whole file system for the Input. It was a nice hack, and a good teardown.
Amazon is now offering a stripped-down version of their Echo smart speaker called Input, which teams up with speakers that you already own to satisfy all your privacy invasion needs on the super cheap — only $10. At that price, it’s hard to resist buying one just to pop it open, which is what Brian Dorey did with his. The teardown is pretty standard, and the innards are pretty much what you’d expect from a modern piece of surveillance apparatus, but the neat trick here involved the flash memory chip on the main board. Brian accidentally overheated it while trying to free up the metal shield over it, and the BGA chip came loose. So naturally, he looked up the pinout and soldered it to a micro-SD card adapter with fine magnet wire. He was able to slip it into a USB SD card reader and see the whole file system for the Input. It was a nice hack, and a good teardown.