There’s nothing quite like a deadline to cut through extras and get right at the heart of the problem. Maybe we should all follow Interpreet’s example and stop thinking about automating our homes and just make it in an eight-day hackathon. His talk at the 2019 Hackaday Superconference covers the zero-to-deployment home automation build he finished in the eight days leading up to his move from one continent to another.
Hackaday’s very own Inderpreet Singh found himself pulling up roots and moving from his home in India to teach at Centennial College in Toronto, Canada. He needed a way to keep an eye on his home from afar and the name of the game is IoT. When the only choice is “whatever works right now”, you can learn a lot about simple solutions.
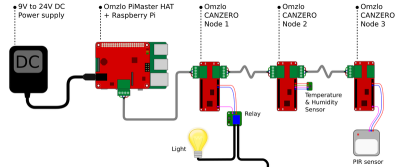
He chose familiar hardware to work with, with the ESP8266 making up the bulk of the nodes and a Raspberry Pi as as a central hub for the setup. He chose to communicate between all the nodes on his system using WiFi because the hardware is robust and available. With security in mind, he keeps the automation system separate from the daily use WiFi system by grabbing an extra access point to serve as the automation network. The Raspberry Pi serves as a router of sorts; its Ethernet port is connected to the IoT device’s AP, while the onboard WiFi is used to connect to the home’s main AP for a connection to the wider Internet.
Software for the system is built on a REST API served by a Python Flask app. Many would advocate for using MQTT but Inderpreet’s testing with that protocol came up short as the broker he intended to use was no longer available. One of the interesting parts of his system design is that all nodes will check in at regular intervals; this allows them to inquire about actions they need to take, but it also allows the system to detect a malfunctioning node immediately. I’ve seen a similar trick used by Elliot Williams where he assigns a “ping” topic to all MQTT devices that causes them to report in with their IP address. Having a system to query and ensure the health of every node is a big tip to take away from this talk.