Lots of people set out to build appliance monitors, whether it be for the fridge, the garage door, or the washing machine. Often, it’s nicer not to cut into an appliance to make direct electrical connections, especially when mains power or water is involved. But how else can we know what the appliance is doing?
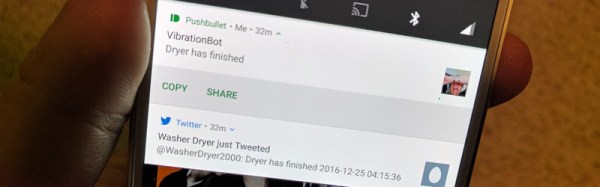
[Drew Dormann] wanted to smarten up his old washing machine, so designed a system that uses a vibration sensor to monitor appliances. It’s a simple build, pairing the 801s vibration sensor with a Raspberry Pi Zero. Naturally, adapter boards are readily available to make hooking things up easy. Then it’s just a matter of tying it all together with a simple Python script which sends notifications using Twitter & PushBullet.
It’s important to note that this approach isn’t just limited to washing machines – there’s a whole laundry list of home appliances that vibrate enough to be monitored in this way! It’s likely you could even spy on a communal microwave in this way, though you might struggle with WiFi dropouts due to interference. Build it and let us know.
[Drew]’s build is a great example of what you can put together in a few hours with parts off the shelf. For those that consider the Pi Zero overkill for this application, consider this vibration-based laundry monitor based on the ESP8266. Think you can do better? Show us what you’ve got on Hackaday.io!