When he needed a gift for his Alien superfan friend, [Stephen Brennan] decided the best way to put his unique set of skills to use would be to create a bootable Linux operating system that captures the sights and sounds of the Nostromo’s retro-futuristic computer systems. We could all use a friend like that.
Even if would never occur to you gift somebody a bootable flash drive, there’s a wealth of information in this blog post about Linux customization which could be useful for all sorts of projects. From creating a bootsplash image to automatically starting up a minimalistic windowing environment so a single graphical application takes center stage.
 Whether you’re looking to tweak your desktop machine or build a Raspberry Pi kiosk, the commands and tips that [Stephen] shows off are sure to be interesting for anyone who’s not quite satisfied with how their Linux distribution of choice looks “out of the box”.
Whether you’re looking to tweak your desktop machine or build a Raspberry Pi kiosk, the commands and tips that [Stephen] shows off are sure to be interesting for anyone who’s not quite satisfied with how their Linux distribution of choice looks “out of the box”.
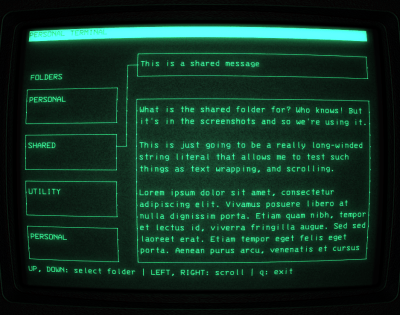
But there’s more to this project than a custom wallpaper and some retro fonts. [Stephen] actually took the time to create a facsimile of the “Personal Terminal” computer interface shown in the recent Alien: Isolation game in C using ncurses. The resulting program, aptly named “alien-console”, is released under the BSD license and is flexible enough that you could either use it as a base to build your own cyberpunk UI, or just load it up with custom text files and use it on your cyberdeck as-is.
Finally, to really sell the Alien feel, [Stephen] went through and ripped various audio clips from the film and wove them into the OS so it would make the movie-appropriate boops and beeps. He even included a track of the Nostromo’s ambient engine noise for proper immersion. But perhaps our favorite trick is the use of the sleep command to artificially slow down the terminal and give everything a bit more “weight”. After all, flying a pretend starship should feel like serious business.